- We’ll be at RSA Conference 2026, Moscone Center, San Francisco | 23rd - 26th March, 2026 | N-6473
High speed and real-time passive interception platforms for lossless data extractions with next-gen DPI probe, delivering effective intelligence and security.
360 degree view of adversaries by providing a unified view of all intercepted data on a single interface.
Capabilities powered by AI such as Audio Analysis, Text Capabilities, Predictive Analysis, Pattern Recognition and more.

Ingest data from a variety of sources - whether structured or unstructured. IntelliWorker ETL framework enables template driven data ingestion so that all data is normalized and analyzed for consistency in quality of outcome.

A modular design that enables clustering at every level, IntelliWorker can quickly ramp up to support heavy analytics demand or greater ingest pipeline. Support retrospective analysis with 180s response time.

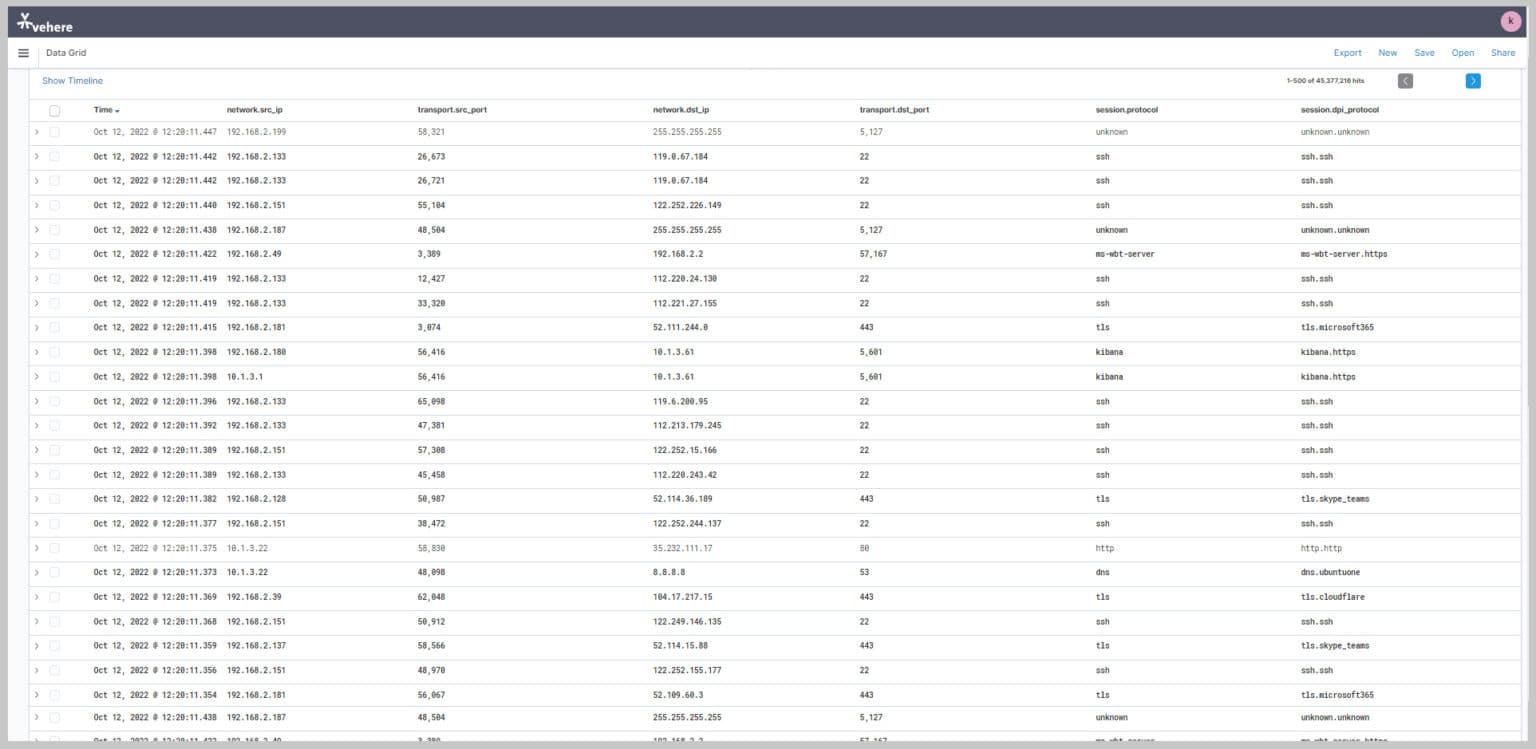
Powerful analytics to search through content by leveraging algorithmically created metadata eliminating the need for analyst review of content thereby saving considerable time, effort and, compute.
High Performance Network Analytics enables collection and analysis of mass, wide, and target data from diverse communication network sources, including telephone calls, mobile data, and Internet-based services such as email, voiceover-IP, instant messaging, and others.
High Performance Cybersecurity detects and contains post-breach activities. It ensures full visibility with lossless packet capture, full digital forensics, next-gen file analysis, AI-powered breach detection and threat hunting.
Vehere’s technology strengthens national security without compromising constitutional privacy protections, embodying the core principle of ‘Protection with Privacy’.
High speed and real-time passive interception platforms for lossless data extractions with DPI engine
Behavior-based protocol detection of thousands of protocols
Open Architecture which is scalable, secure, and standards-based
AI/ML-based advanced analytics for data analysis and cyber threat detection
Deployment adaptability available for installation on customer-provided hardware or on Vehere-certified hardware systems
Supports complex and high-volume networks
Centralized monitoring/ processing of target related activity
Next-gen Malware Lab for improved threat intelligence
• Reliable and continuous collection across a wide range of communication network sources and technologies
• Automatically focus on the most relevant sources for efficient coverage management and resource allocation
• AI-powered analytics to identify relations, interests, activities, patterns and abnormalities
• Detect and highlight suspicious indicators, unique insights and new patterns
High Performance Network Analytics
Network Intelligence Analytics help protect nation and its citizens by collecting mass, wide and target data from diverse communication network sources.
High Performance Cybersecurity
Massive scale Network Security for national critical infrastructure that detects and contains post-breach activities using AI/ML and heuristic behaviour analytics.
Zero-Day Defender
Advanced file analysis system providing a complete picture of potential
threats by comprehensively monitoring every aspect of a file's behavior
across various critical areas.
Fusion Analytics
Leverage the power of Advanced automation technologies including artificial intelligence/machine-learning and, behaviour-based Rule-Engine learning to rapidly fuse all your data and extract critical insights.
Fiber IP Monitoring
Works on advanced automation technique for accessing big data carried over large scale optical transport networks. Provide comprehensive optical network analytics, both real-time and historical, using metadata extracted
across the entire transport network
Mass Network Intelligence
Lawful Capturing and Monitoring System is a state-of-the-art monitoring solution that assists Communication Service Providers in complying with electronic monitoring law enforcement orders.
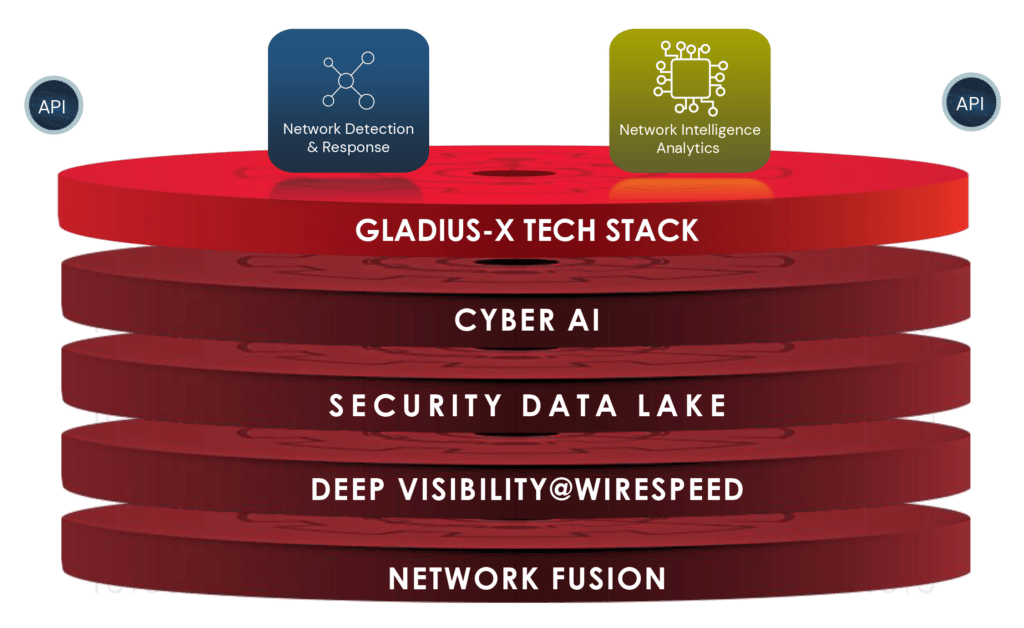
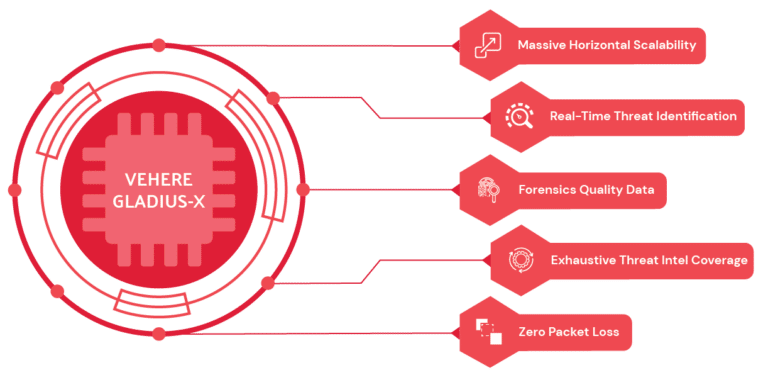
The "Gladius-X", a Vehere’s exclusive intellectual and proprietary tech-stack for fighting against deadliest threat actors and dreadful anomalies.
AI-powered Language identification (supporting 99 languages) aids in transcription and translation in Audio and Speech to Text Conversions. Allows analysts to efficiently process recorded audio files.
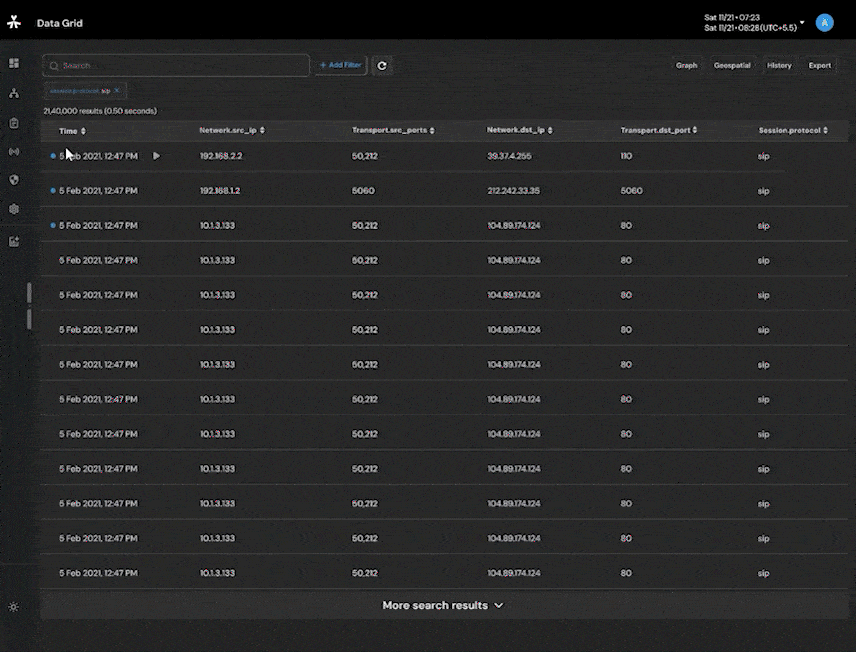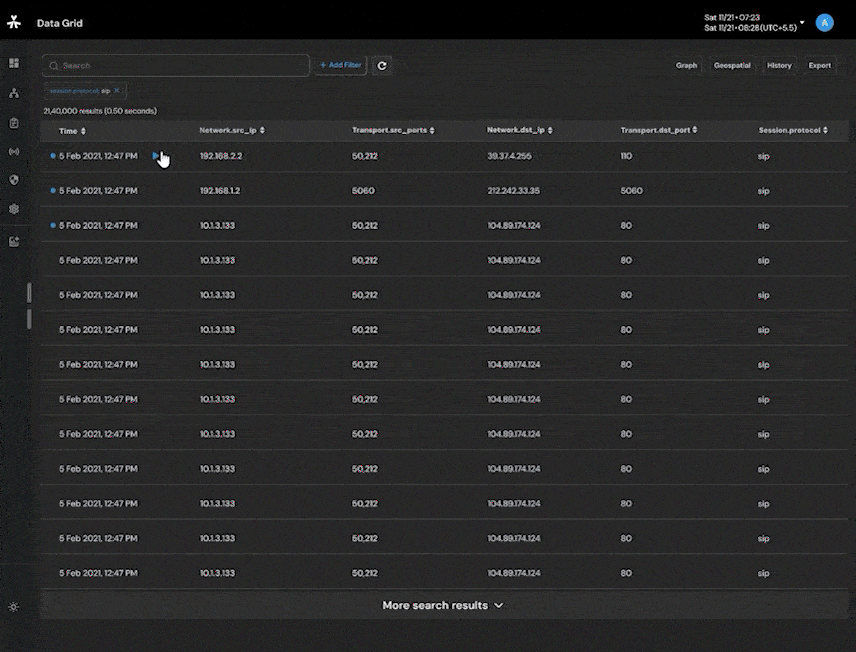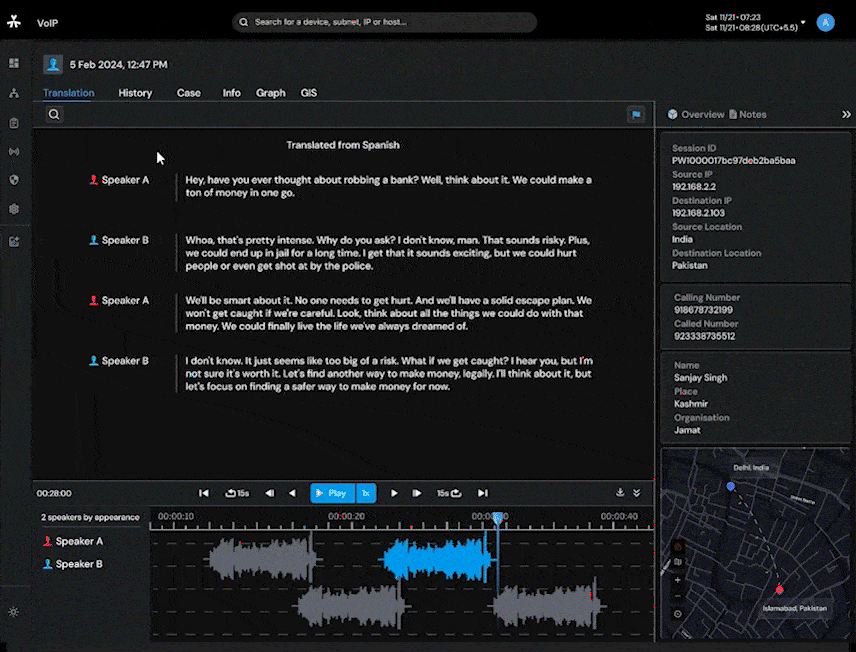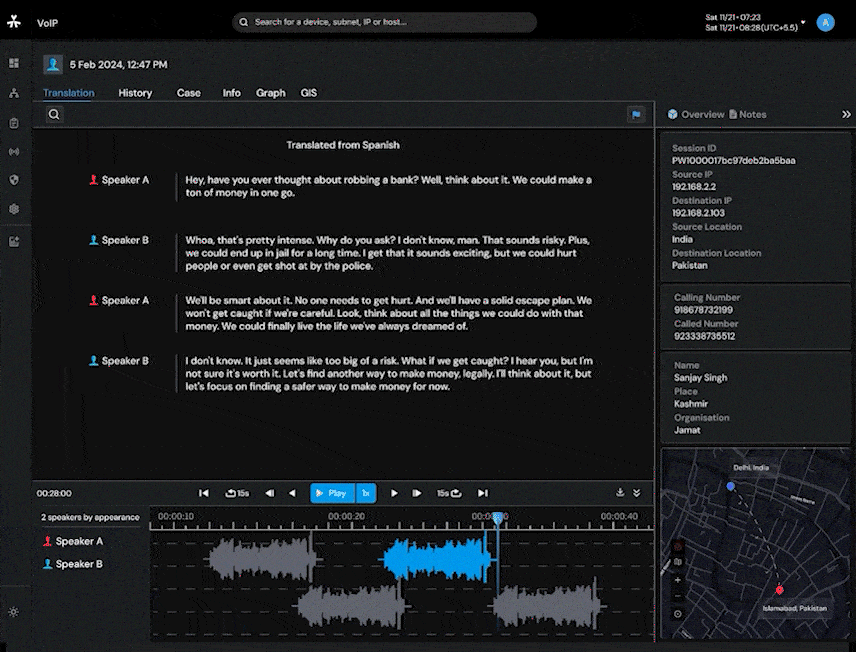
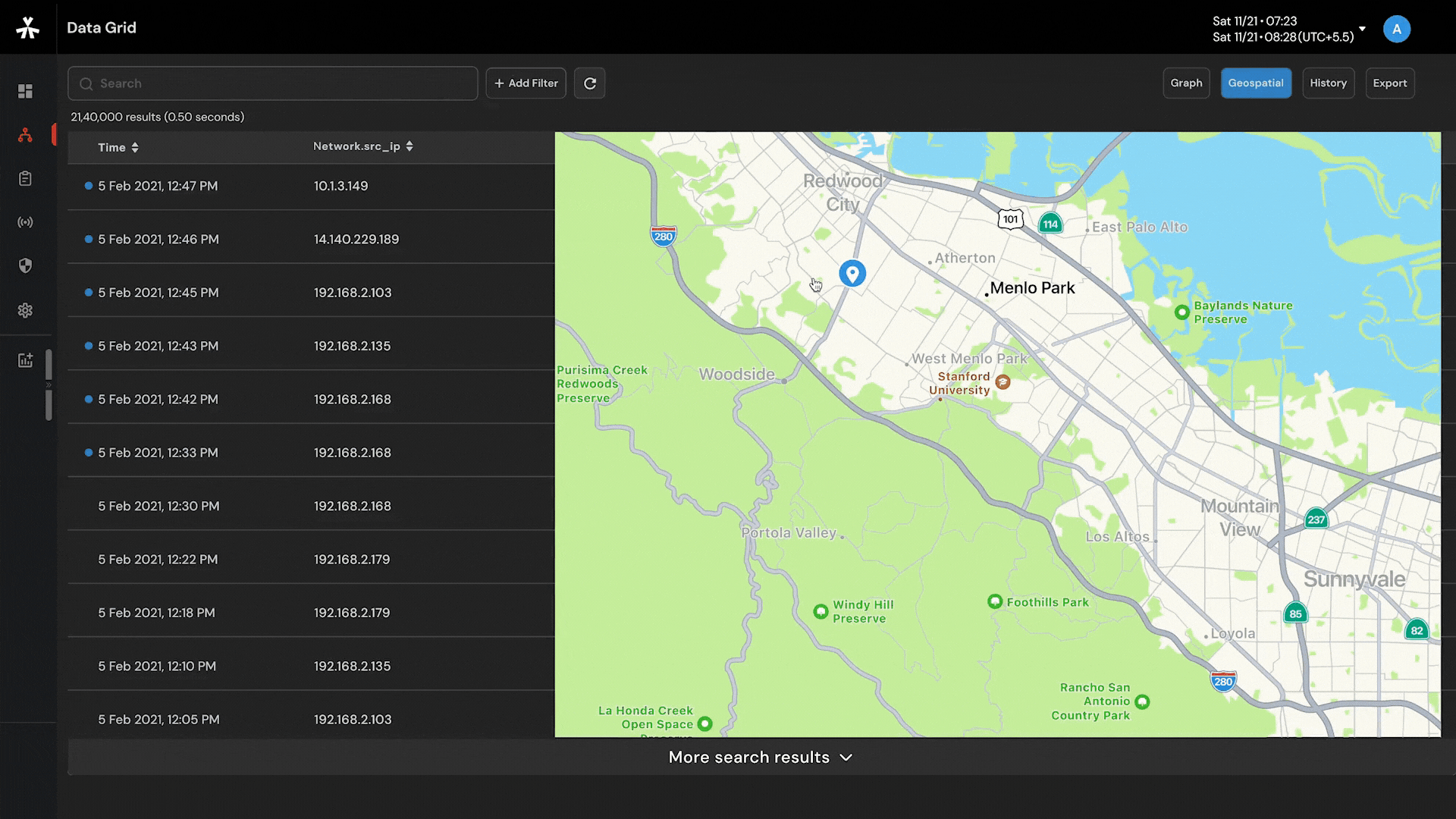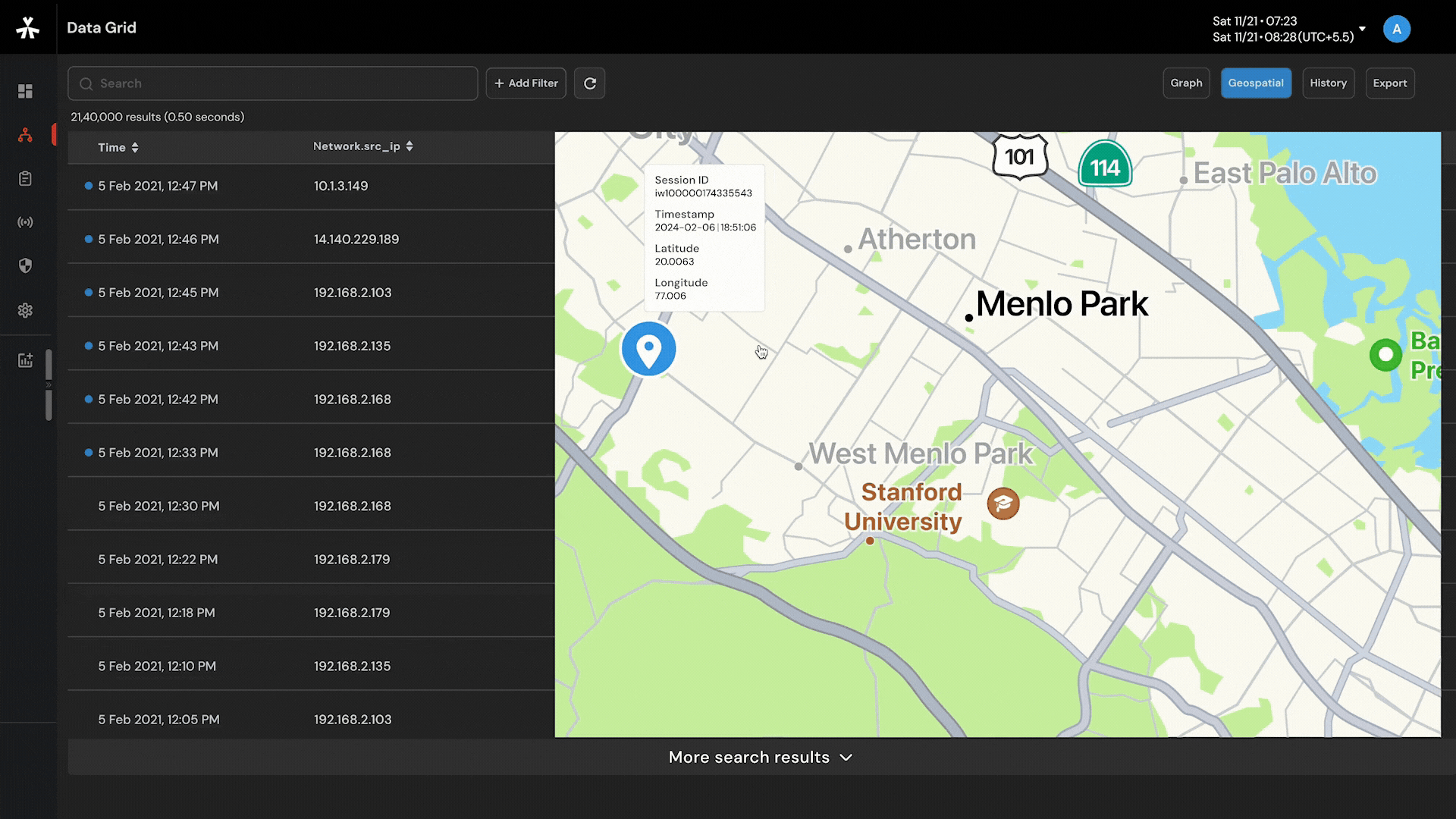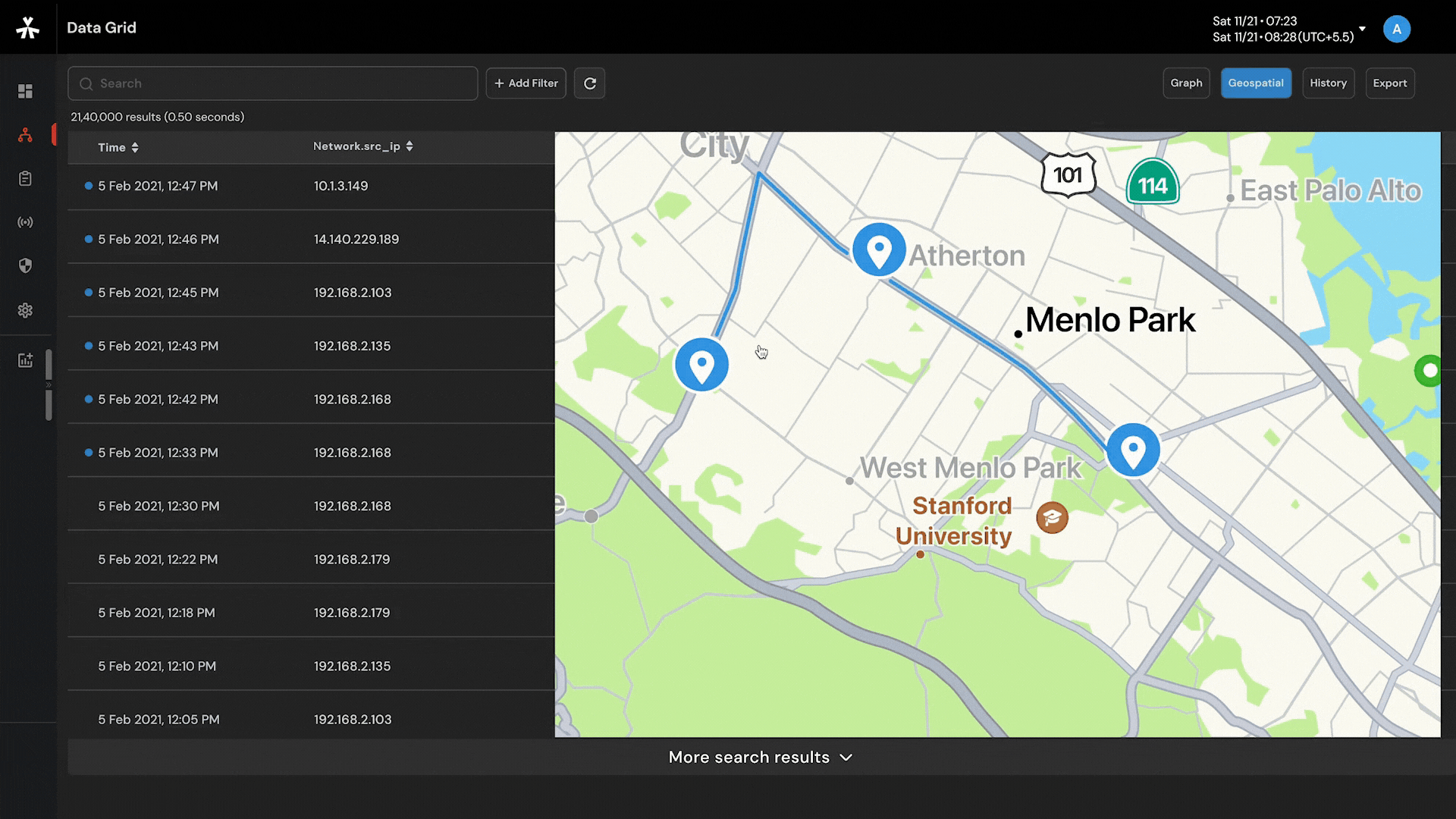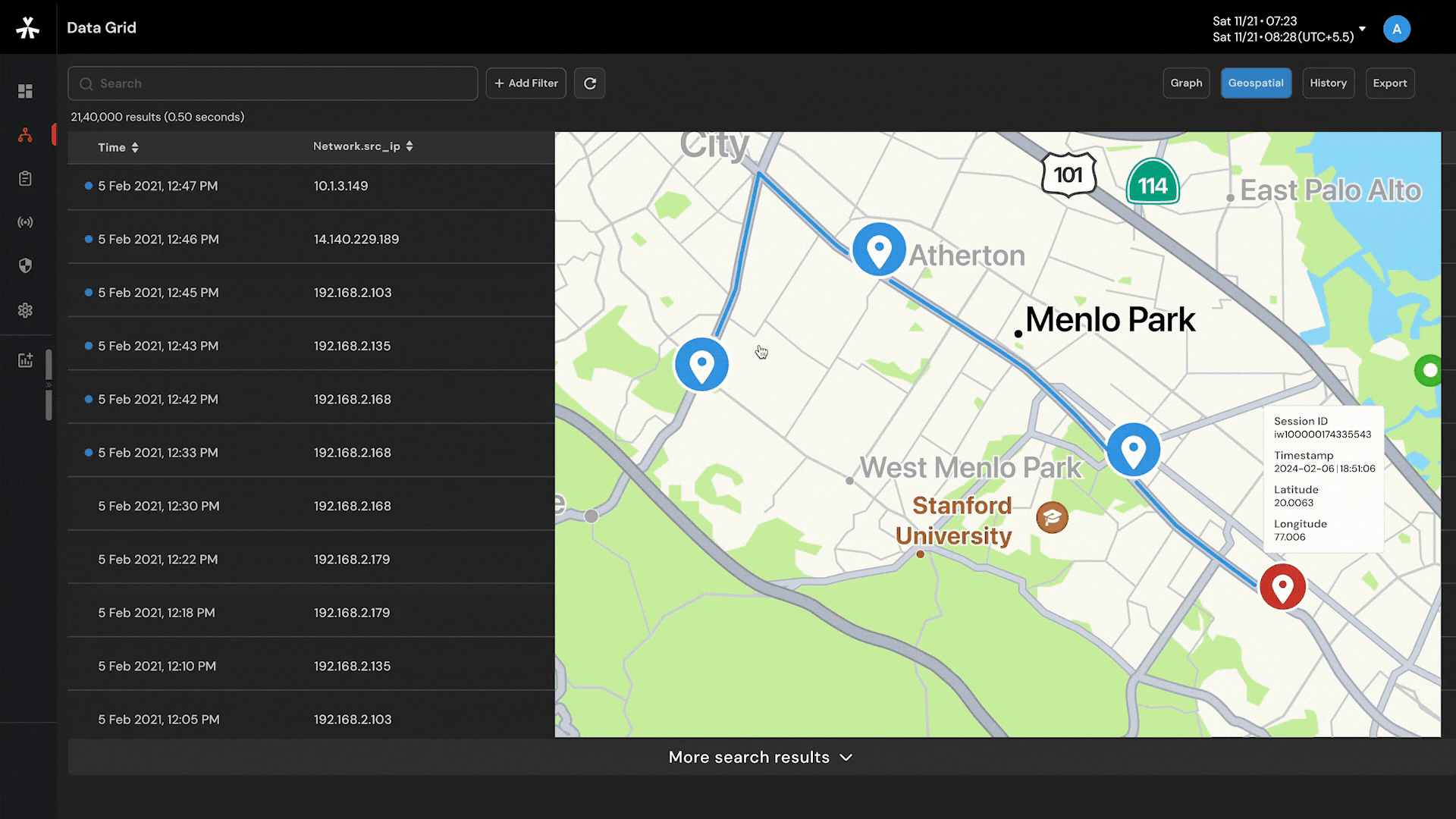
Target movement analysis and geofencing by harnessing the power of a 16-layer street view offline map.
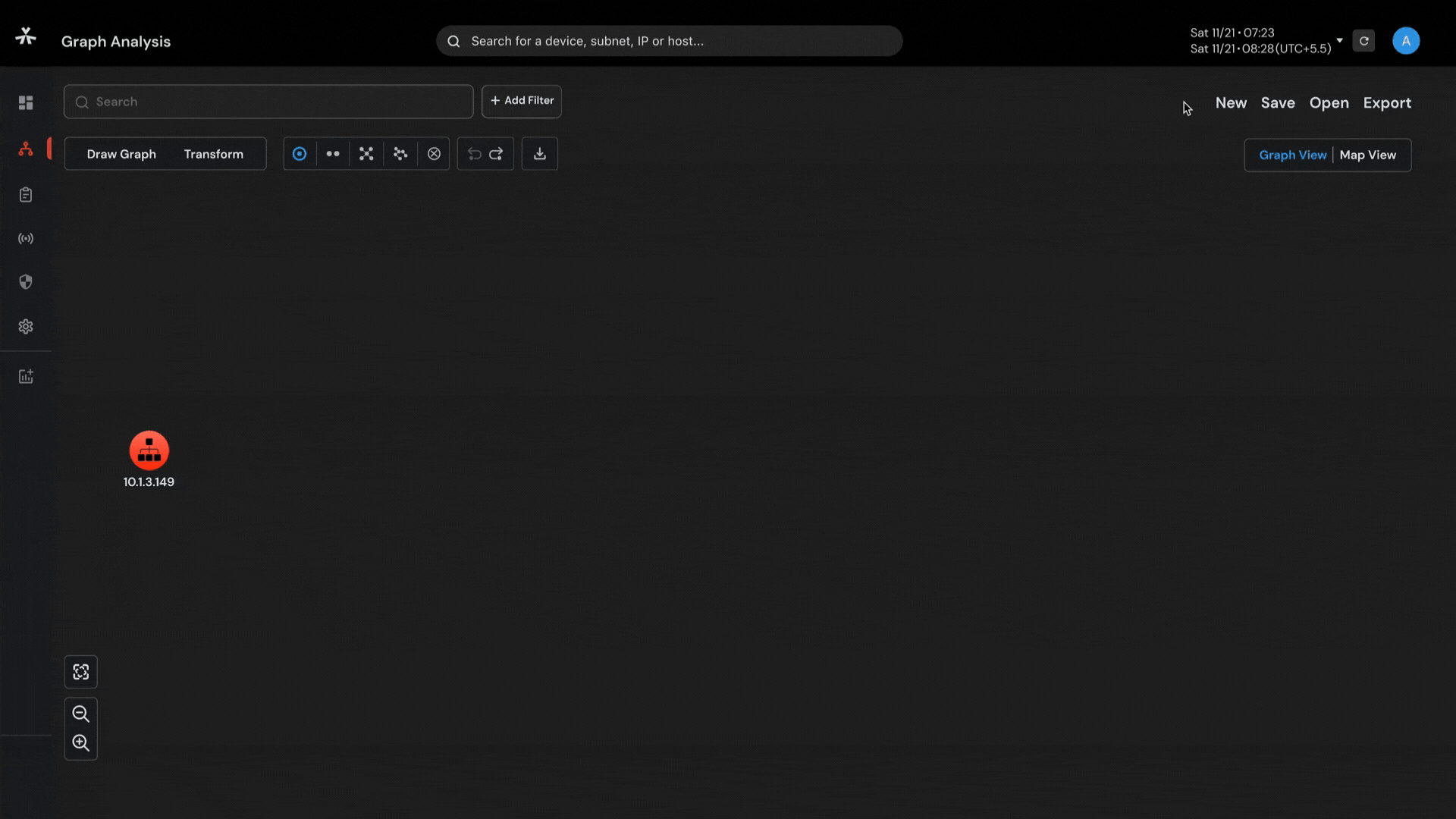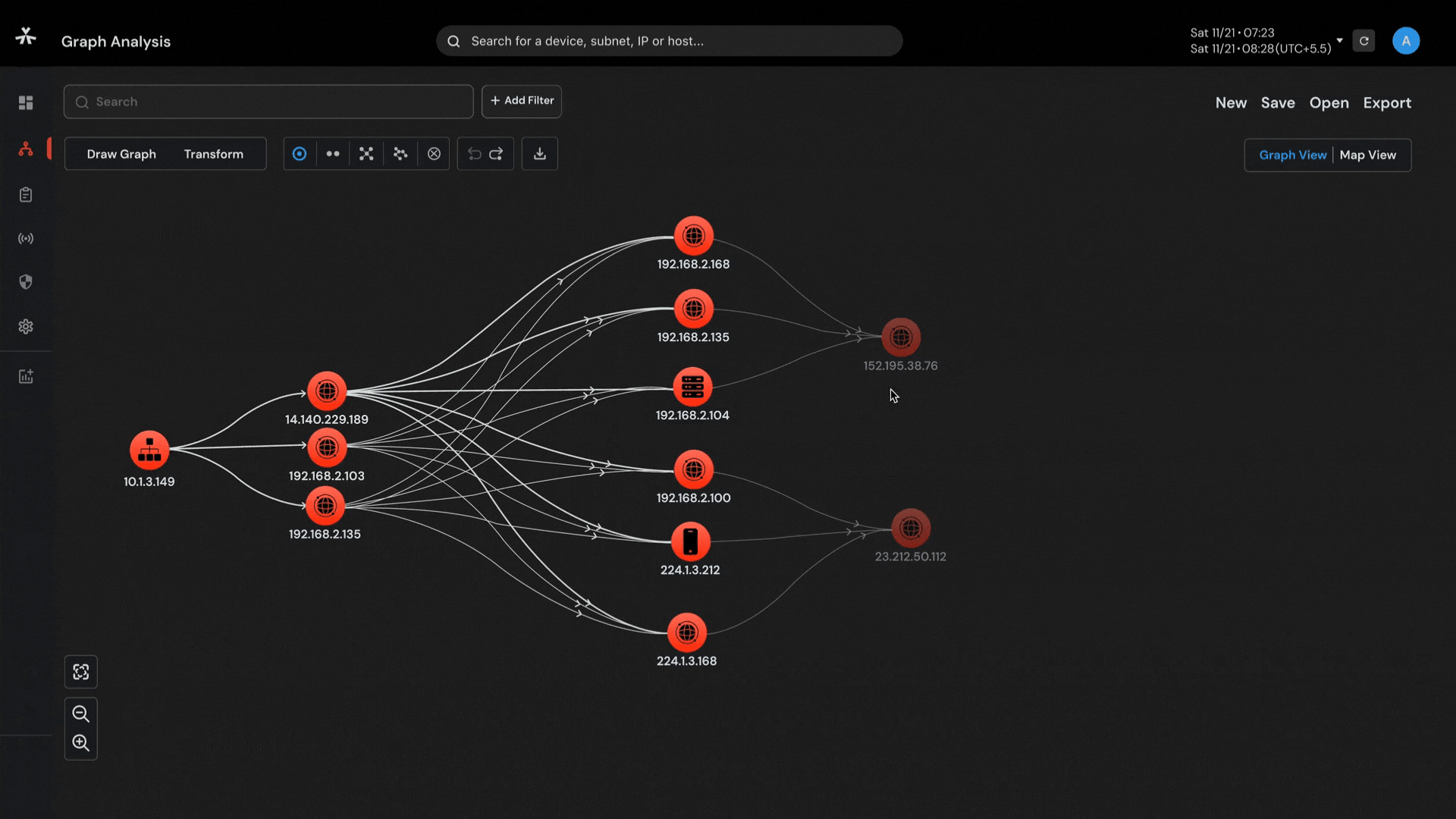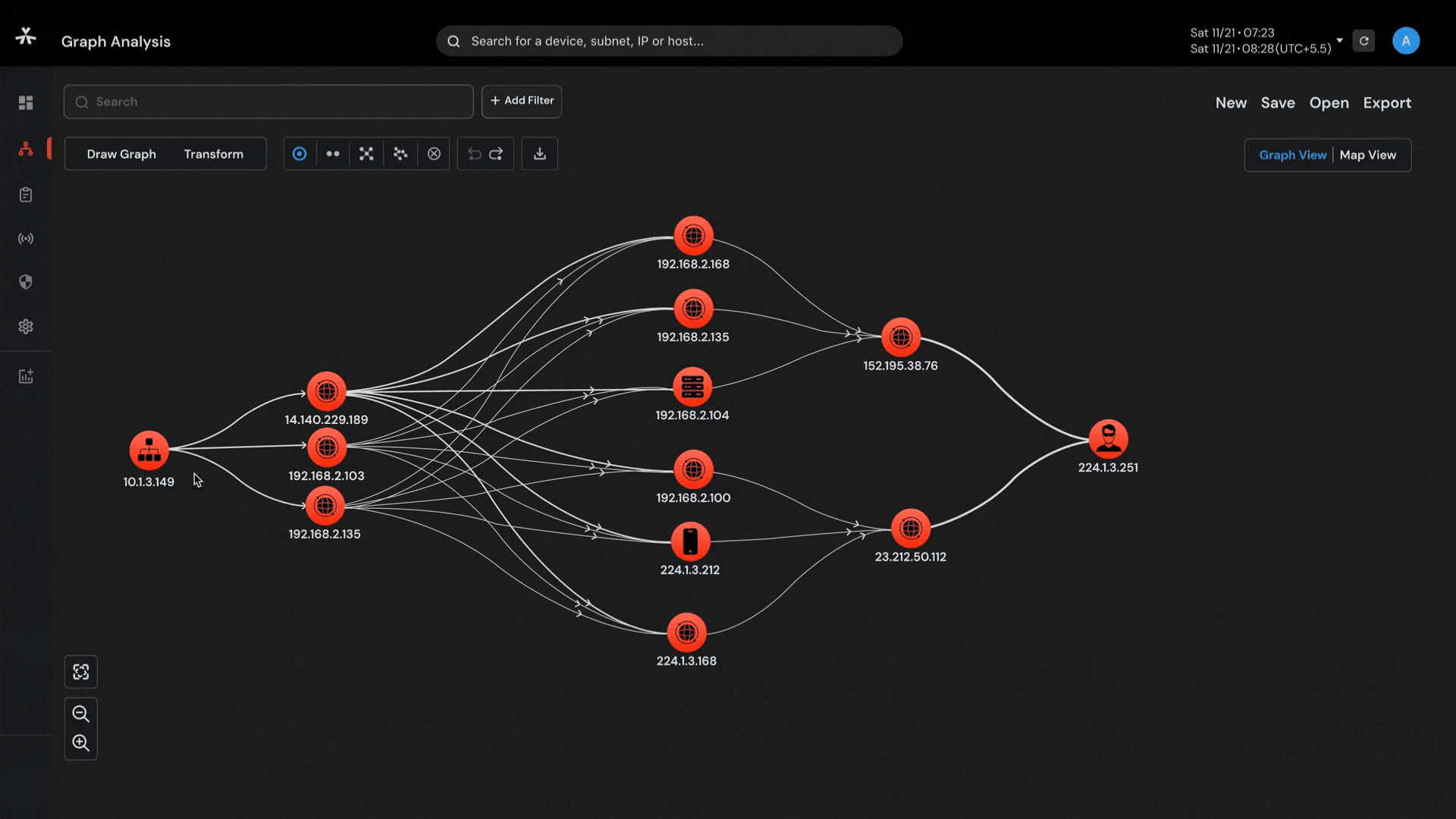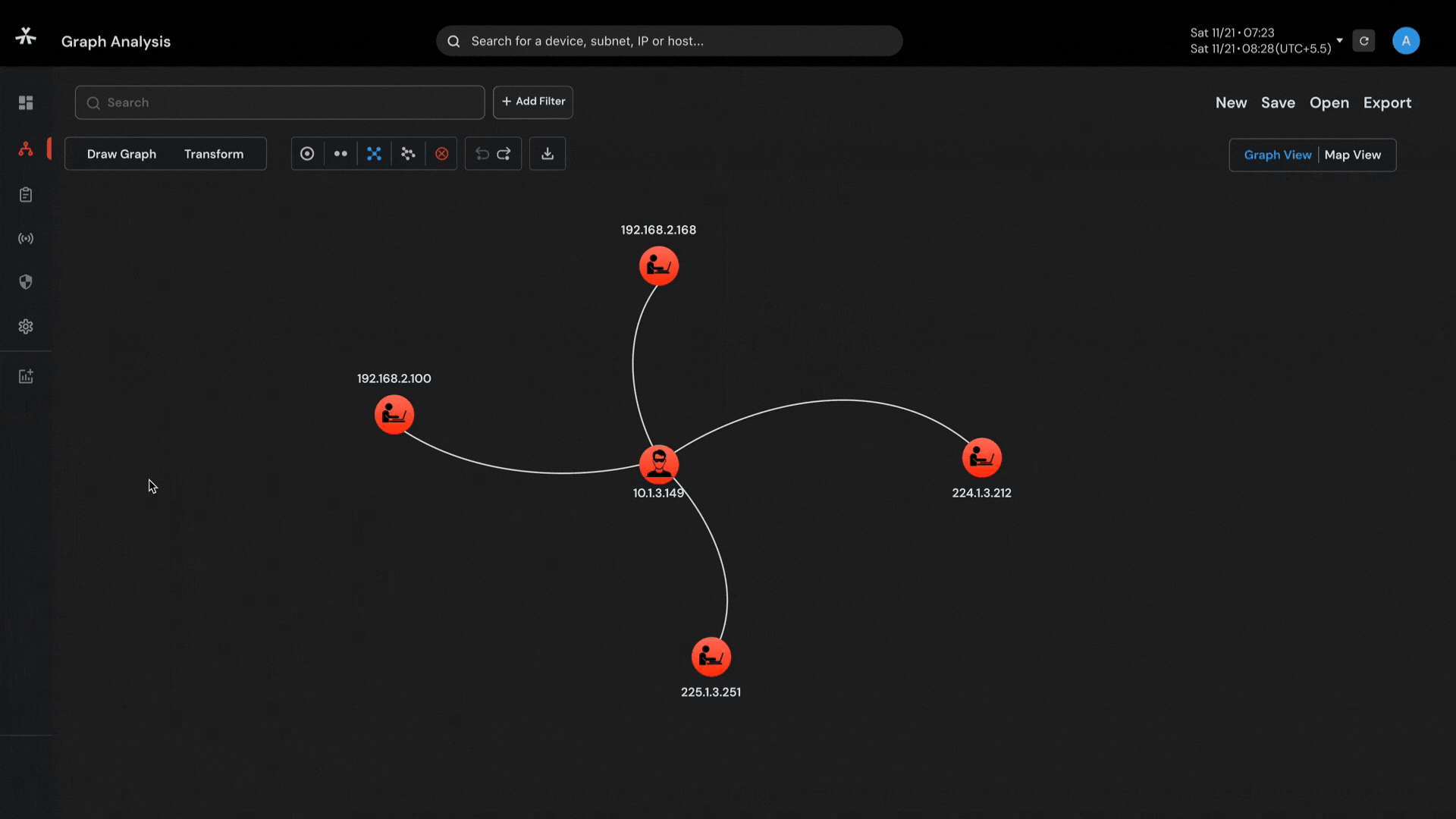
Capability to visualize complex networks with 6-layered graph analysis and connect the dots so that nothing remains hidden.
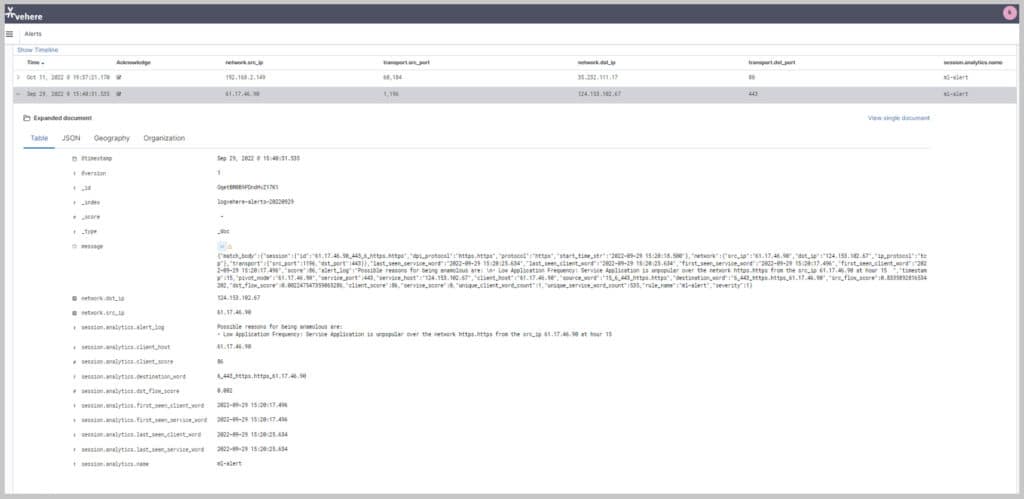
• Manual inspection of content is time-consuming and often error-prone.
• Without opening the content (that may actually be weaponized), IntelliWorker enable discovery across many thousands of documents to identify extent of leak of sensitive information in communication channel.
Capability to visualize complex networks with 6-layered graph analysis and connect the dots so that nothing remains hidden.
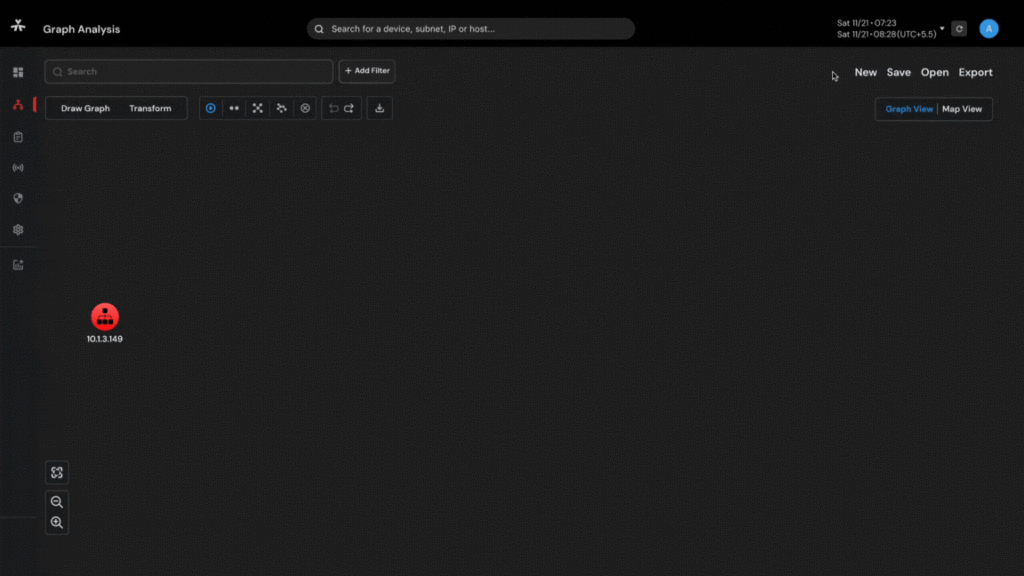
• Encryption is a challenge for LEAs. Even the content may be encrypted.
• Vehere's NI enables analysis using statistical techniques enabling identification of origins.
• Special fingerprinting techniques enable identification of device and owner.
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |