Introduction
The Traffic Management User Interface (TMUI) of F5 BIG-IP has a significant remote code execution (RCE) vulnerability known as CVE-2020-5902.
The vulnerability stemmed from a flaw in the TMUI’s handling of specific URI (Uniform Resource Identifier) requests. Essentially, the TMUI failed to properly sanitize user-supplied input, allowing attackers to inject arbitrary commands into the underlying operating system.
By taking advantage of this vulnerability, attackers can totally compromise impacted devices, run arbitrary system commands, and obtain root access. This vulnerability has been extensively targeted in the wild because of its CVSS score of 10.0.
This incident highlights the critical importance of promptly patching security vulnerabilities, especially in network devices that are exposed to the internet.
Hence, it is imperative that organizations have robust vulnerability management and incident response plans in place to successfully identify and stop exploitation attempts.
What is CVE-2020-5902?
A path traversal and RCE vulnerability known as CVE-2020-5902 affects several F5 BIG-IP versions. It gives an unauthorized attacker the ability to remotely take over the system, read files that are forbidden, and run arbitrary instructions.
Detection of CVE-2020-5902 with Suricata IDS/IPS Rule:
To detect exploitation attempts of CVE-2020-5902, the following Suricata IDS/IPS rule can be deployed:
How It Works:
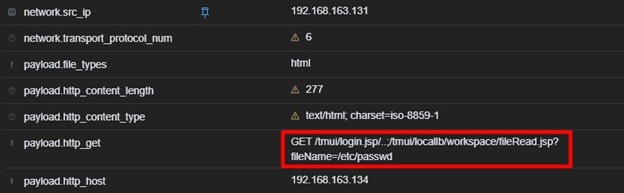
- Detects HTTP requests containing “/tmui/login.jsp/..;”, a key indicator of directory traversal attempts.
- Looks for “/tmui/locallb/workspace/fileRead.jsp?fileName=”, which is used to read sensitive system files.
- Triggers an alert when an exploitation attempt is detected.
CVE-2020-5902 alerts:

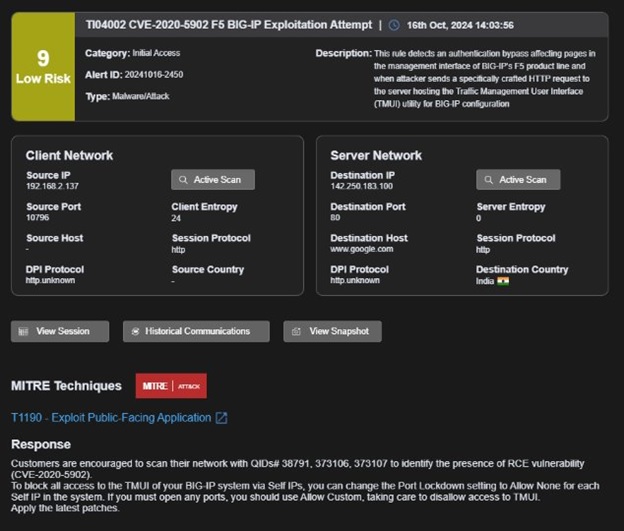
As shown in the following data grid:
Impact and Consequences:
- Attackers could steal sensitive data stored on or passing through the BIG-IP device.
- Attackers could disrupt critical services by taking the BIG-IP device offline or manipulating its configuration.
- Once inside the network, attackers could use the compromised BIG-IP device as a pivot point to attack other systems.
- Attackers could install malware on the BIG-IP device or other systems on the network.
Mitigation
CVE-2020-5902 is a serious vulnerability that can lead to full system compromise if left unpatched. Organizations should:
✅Apply patches immediately to secure their BIG-IP systems.
✅Restrict access to TMUI, ensuring it is not exposed to the internet.
✅Deploy IDS/IPS rules like the one above to detect and block exploitation attempts.
✅Regularly scan your network for vulnerabilities.
Conclusion:
The threat landscape keeps evolving, and Vehere’s security research wing, Moon Treader, is actively investigating and developing content on a regular basis.
The team will continue to monitor the latest developments in the cyberthreat landscape and keep upgrading the detection capabilities to improve the security posture of Vehere’s customers.
So, to stay protected, apply the patch today and subscribe for the latest security alerts.