Introduction:
A remote code execution (RCE) vulnerability has been discovered in Fortra GoAnywhere MFT, a managed file transfer solution. This vulnerability, identified as CVE-2023-0669, enables attackers to inject malicious code into the system. Notably, it has been exploited in the wild, raising significant security concerns.
Understanding CVE-2023-0669:
CVE-2023-0669 is a critical vulnerability found in Fortra GoAnywhere MFT. Discovered by security researchers, it allows attackers to execute arbitrary code remotely. This type of vulnerability can lead to severe security breaches, including unauthorized access to sensitive data and system control.
Vulnerability Trigger:
The proof-of-concept code used for exploitation is given below:
POST /goanywhere/servlet/compliance HTTP/1.1
Host: vulnerable-system.com
Content-Type: application/x-www-form-urlencoded
Content-Length: 128
param1=value1¶m2=value2¶m3=<malicious_code>
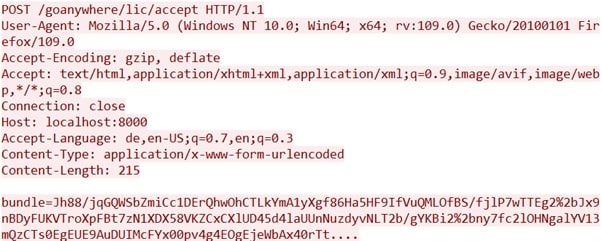
To exploit CVE-2023-0669, attackers need access to the administrative console. The PoC shows a malicious POST request sent to the device, leading to remote code execution.
How Attackers Exploit the Vulnerability
Exploiting CVE-2023-0669 involves several steps:
- Accessing the Admin Console: Attackers must first gain access to the admin console.
- Crafting Malicious Requests: Using the PoC code, attackers send specially crafted requests.
- Executing Malicious Code: The server processes the request, executing the embedded malicious code.
Real-world cases have shown the consequences of successful exploitation, including unauthorized system control and data breaches.
Threat Severity:
According to Vehere’s threat severity scale, CVE-2023-0669 is classified as High. This classification is due to its potential for severe damage and ease of exploitation. The vulnerability is also listed in the CISA known vulnerabilities catalog, highlighting its significance.
Potential Impact on Systems:
The impact of CVE-2023-0669 on affected systems is substantial. It can lead to:
- Unauthorized access and control over the system
- Data breaches and loss of sensitive information
- Disruption of business operations.
Historical examples of similar vulnerabilities have caused significant financial and reputational damage to organizations.
Detection and Mitigation Strategies:
Vehere’s security research wing, Moon Treader, has defined a rule to detect this malicious activity: TI03163 Fortra GoAnywhere Managed File Transfer RCE CVE-2023-0669. To mitigate the risk, it is crucial to:
- Patch Systems: Ensure all systems are updated with the latest security patches.
- Apply Workarounds: Follow Fortra’s recommended workarounds until patches are applied.
Vehere’s Security Research Wing – Moon Treader:
Moon Treader plays a critical role in identifying and mitigating vulnerabilities. The team actively researches and develops detection capabilities to address emerging threats. Their ongoing efforts ensure that Vehere’s customers are protected against the latest cyber threats.
Best Practices for Preventing Exploitation:
To prevent exploitation of vulnerabilities like CVE-2023-0669:
- Keep Systems Patched: Regularly update all software to the latest versions.
- Conduct Security Audits: Perform routine security audits to identify and address potential weaknesses.
- Educate Staff: Provide security training to staff to recognize and respond to threats.
Vehere AI Network Security:
Vehere AI Network Security combines Network Detection & Response (NDR) and Network Forensics to provide comprehensive protection.
Network Detection & Response (NDR):
NDR uses behavioral analytics and AI/ML to detect abnormal system behaviors, helping to contain post-breach activities such as ransomware, APTs, and insider threats.
Network Forensics:
Network forensics supports incident response by analyzing and reconstructing attack timelines. It provides evidence for legal proceedings and helps in understanding the source of incidents.
Gartner Recognition:
Vehere has been recognized in two 2023 Gartner® reports: “Emerging Tech: Top Use Cases for Network Detection and Response” and “Emerging Tech: Security—Adoption Growth Insights for Network Detection and Response.” This recognition underscores Vehere’s importance in modern security landscapes.
Conclusion:
CVE-2023-0669 represents a significant threat, but with proactive measures, organizations can protect themselves. Moon Treader’s continuous efforts in vulnerability detection and Vehere’s robust security solutions offer a strong defense against such vulnerabilities. It is essential to stay updated and follow best practices to maintain a secure environment. The threat landscape is continuously evolving. Moon Treader’s ongoing research and development efforts ensure that detection capabilities are always up to date, enhancing the security posture of Vehere’s customers.
FAQs:
- What is CVE-2023-0669?
CVE-2023-0669 is a remote code execution vulnerability found in Fortra GoAnywhere MFT, allowing attackers to inject and execute malicious code. - How can CVE-2023-0669 be exploited?
Attackers exploit CVE-2023-0669 by accessing the administrative console and sending specially crafted POST requests that contain malicious code. - What are the potential impacts of this vulnerability?
The impacts include unauthorized system access, data breaches, and disruption of business operations. - How can I protect my system from this vulnerability?
Protect your system by applying the latest patches, following recommended workarounds, and conducting regular security audits. - What role does Vehere play in detecting and mitigating this threat?
Vehere’s security research wing, Moon Treader, has developed detection rules for this vulnerability and provides ongoing research to enhance security measures. - Why is it important to keep systems patched and updated?
Regular updates and patches ensure that known vulnerabilities are fixed, reducing the risk of exploitation and improving overall security.