Introduction
Ransomware has become one of the most pressing cybersecurity threats, with GandCrab ransomware being a notorious variant that wreaked havoc and infected thousands of systems, extorting victims by encrypting their files and demanding ransom payments in cryptocurrency.
As with many malware families, creating various rules for ransomware detection and mitigating GandCrab’s activity is critical for organizations. These rules are designed to identify patterns of behavior associated with GandCrab infections, ensuring prompt response and minimizing damage.
Why Multistage Detection Is Critical for GandCrab
There are a variety of malwares that use a variety of techniques. Some of these techniques are very common, and writing a detection for them may lead to false positives. Multistage detection leverages a combination of different indicators of compromise (IOCs) and behavior-based analytics to more accurately detect suspicious activities. So, if one combines various such techniques, they can effectively help in identifying and investigating malicious behavior on the network.
This blog outlines GandCrab, the multistage detection rules designed for it, and how they contribute to ransomware defense mechanisms.
What Makes GandCrab Such a Potent Threat?
GandCrab is a ransomware family that quickly became infamous due to its widespread infection methods and innovative business model. It operates as a Ransomware-as-a-Service (RaaS), where developers distribute the malware to affiliates who, in turn, launch attacks in exchange for a percentage of the ransom.
GandCrab initially gained notoriety due to its rapid release cycle, with frequent updates to evade detection. It employs various distribution techniques, including phishing emails, exploit kits, and malicious websites. Once a system is infected, GandCrab encrypts files using a combination of AES and RSA encryption algorithms. The attackers demand a ransom, payable in cryptocurrency (usually DASH or Bitcoin), in exchange for a decryption key.
Security researchers, law enforcement agencies, and cybersecurity companies focused on tracking and dismantling the GandCrab operation. Over time, detection techniques evolved, culminating in a set of correlation rules that were used to identify GandCrab infections early in their lifecycle.
Characteristics of GandCrab Ransomware
Based on the packet captured, one can observe various anomalies, such as:
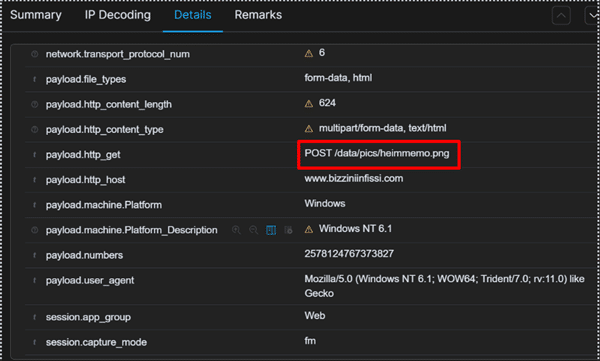
- Posting Data to Image Files: GandCrab often disguises its malicious payload by sending data in what appears to be image file formats. This is an unusual network activity that raises red flags for those monitoring traffic.
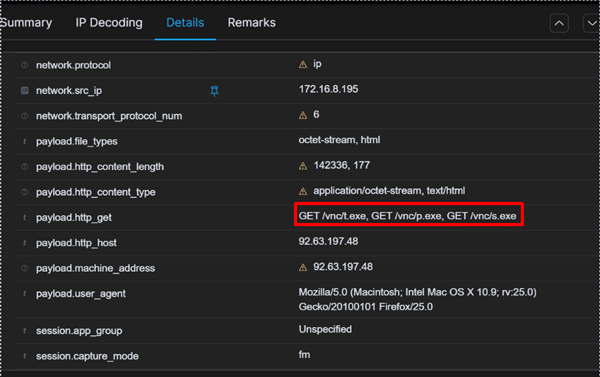
- Downloading Executables from IP Addresses: GandCrab attempts to download executable files from suspicious IPs as part of its infection process. Monitoring traffic to identify these downloads is crucial.
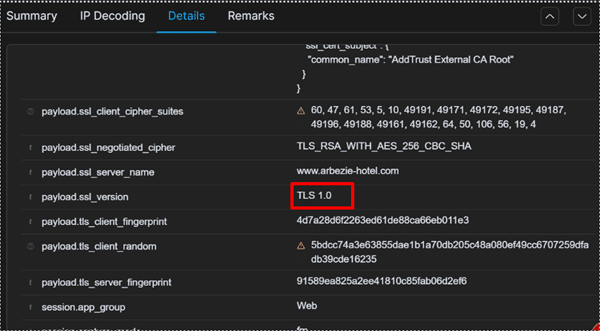
- Use of Old TLS Versions: GandCrab often communicates using outdated TLS versions. While many attackers switch to newer encryption protocols, GandCrab’s persistence with old versions can signal its presence.
If these anomalies are combined, then one can detect activity related to GandCrab ransomware.
GandCrab Detection Rules by Vehere NDR
Vehere Network Detection and Response (NDR) technology has crafted a set of rules designed specifically to identify GandCrab ransomware by correlating suspicious activities.
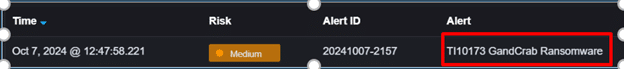
Here is how it looks when the final alert triggers:
GandCrab alert
Here are various activities which are used by GandCrab ransomware:
- Exe file Download from IP Address
- Old TLS version being used
- Post to Image file extensions
Vehere NDR excels by combining these behaviors through correlation. Correlation detection links multiple indicators—such as unusual traffic patterns, suspicious file downloads, and outdated encryption use—to determine when an attack is likely taking place. This holistic approach reduces the risk of false positives while increasing the ability to detect sophisticated ransomware like GandCrab early in the attack lifecycle.
When these correlations are observed, the system triggers a “TI10173 GandCrab Ransomware” alert, allowing security teams to act swiftly to mitigate the threat.
Safeguarding Against GandCrab Ransomware
GandCrab may have been one of the most notorious ransomware variants, but with advanced detection techniques like Vehere’s correlation rules, security teams are better equipped than ever to mitigate its impact. By focusing on behavioral patterns and combining multiple indicators of compromise, these rules offer an effective means of combating not only GandCrab but other ransomware threats as well.
The ability to track behaviors such as executable downloads from suspicious IPs, use of outdated encryption protocols, and unusual data posting activities forms a strong defense against evolving cyber threats.
Vehere AI Network Security:
Vehere AI Network Security is a unified solution of Network Detection & Response and Network Forensics that acts as the “Second Line of Defense” to protect the corporate networks from the most advanced cyberattacks.
FAQs
- How does GandCrab ransomware spread?
GandCrab spreads through phishing emails, exploit kits, and malicious websites, infecting systems by encrypting files and demanding a ransom for decryption.
- What is Ransomware-as-a-Service (RaaS)?
Ransomware-as-a-Service (RaaS) refers to a business model where ransomware developers rent out their malware to affiliates who carry out attacks. GandCrab operated on this model.
- How does Vehere NDR detect GandCrab?
Vehere NDR detects GandCrab by correlating behaviors like EXE downloads from suspicious IPs, use of old TLS versions, and data posting to image files.
- Why is multistage detection important?
Multistage detection combines multiple indicators of compromise to create a more accurate picture of malicious activity, reducing false positives and improving detection rates.
- Can GandCrab still be a threat in 2024?
While law enforcement has dismantled GandCrab’s operations, variants of the ransomware may still exist. Advanced detection systems like Vehere NDR remain essential in identifying these threats.
- What is the role of correlation in ransomware detection?
Correlation helps by combining multiple suspicious behaviors to identify ransomware attacks more accurately and faster than single-indicator systems








