Introduction:
Vehere’s security research wing, Moon Treader, remains dedicated to enhancing the security of the entire ecosystem through continual software fuzzing efforts. In April 2023, the team uncovered a vulnerability in a popular image manipulation software, which they explained in a blog post. Furthermore, the team recently came across another vulnerability through continuous fuzzing within ImageMagick, duly recognized as CVE-2023-3428 by RedHat. This blog provides an in-depth root-cause analysis of this recently identified vulnerability.
Executive Summary:
ImageMagick is a popular image manipulation software. In the month of June, Vehere’s security research wing responsibly reported the issue to ImageMagick that was in the parsing of specially crafted TIFF files. This issue occurred because ImageMagick did not allocate the required amount of memory and later tried to read data past the allocated memory buffer.
https://github.com/ImageMagick/ImageMagick
The vulnerability was assigned the CVE ID of CVE-2023-3428 by RedHat and was quickly fixed by Imagemagick team in the following patch:
https://github.com/ImageMagick/ImageMagick/commit/a531d28e31309676ce8168c3b6dbbb5374b78790
Replicating the issue:
In the previous blog here , the steps required to fuzz ImageMagick were documented. Similarly, in this blog, the focus will be on replicating and analyzing the root cause of the issue and how it was fixed.
The issue can be replicated with the following command:
magick poc.tiff /dev/null
poc.tiff is the fuzzed file. On running the above-mentioned command, ImageMagick will crash, and we can see the following call stack:
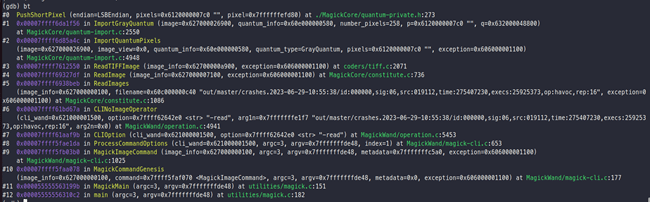
We can see that it is crashing inside the “PushShortPixels” function. On observing the code, one can see that it is crashing while reading the value of pixels:
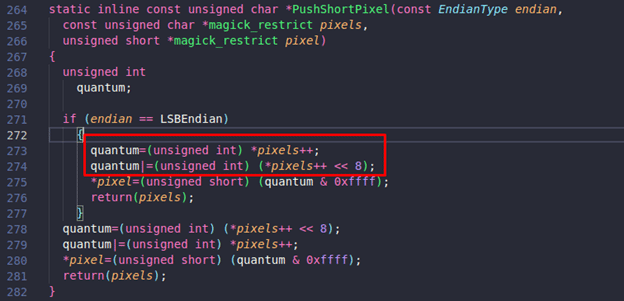
In the above image, one can see that “pixels” is a char *, which points to a memory location. To understand this vulnerability, the following questions need to be answered:
- How is this memory allocated?
- How much memory is allocated?
- Why is the program crashing when accessing this allocated memory?
Debugging the issue:
- How is the memory allocated? How much memory is allocated?
On observing “coders/tiff.c”, one can see the following code:
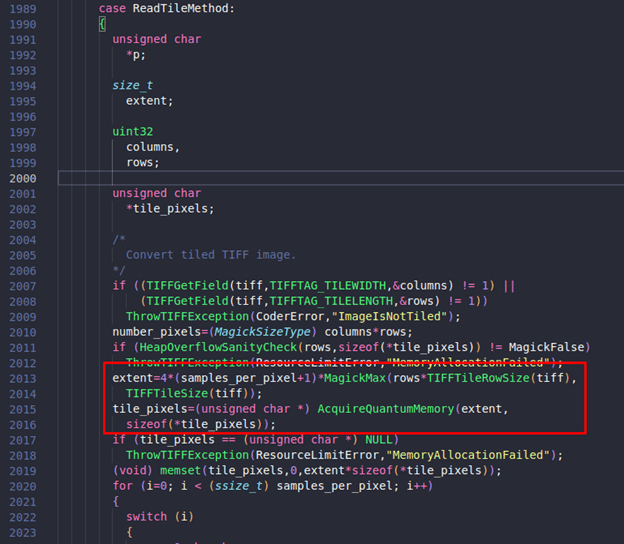
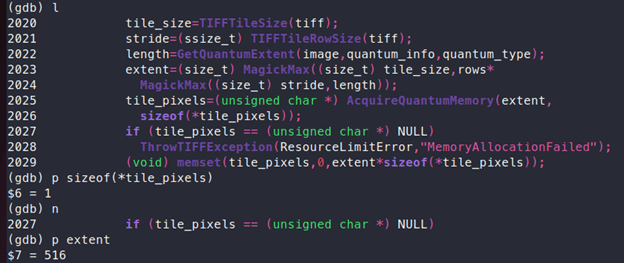
Here, memory is allocated using call to “AcquireQuantumMemory” which takes “extent” and “sizeof(*tile_pixels)”, the values being 264 and 1 respectively, as can be seen in the following screenshot. So, total memory which will be allocated is 264 bytes:
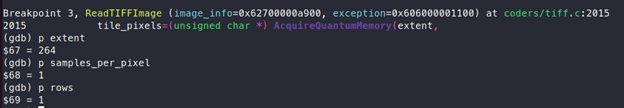
“tile_pixels” will point to this newly allocated memory:
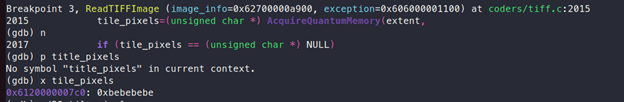
It is to be noted that this memory will contain 0xbe because of ASAN:
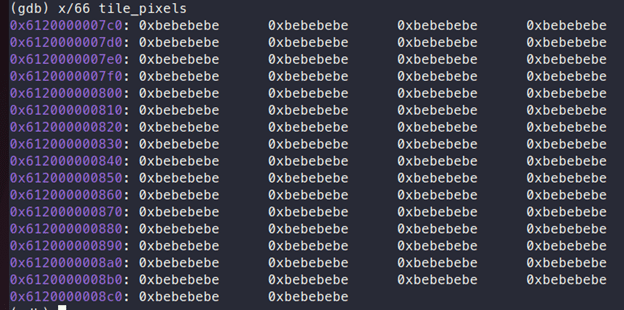
As it is observed, the start address of memory is 0x6120000007c0
The end address of memory is 0x6120000008c7
So, the total memory is: 0x6120000008c7-0x6120000007c0+1 = 264 bytes
- What is the root cause of this vulnerability?
By observing the call stack, we can see that “PushShortPixel” is called “ImportGrayQuantum”:
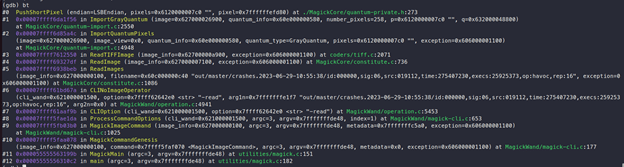
Inside “ImportGrayQuantum”, there is a “for loop” which runs for “number_pixels” time.
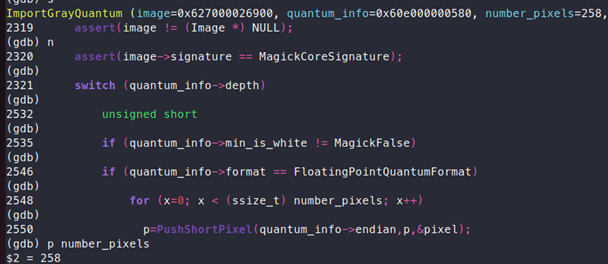
One can see that “number_pixels” is 258 here, and later “PushShortPixel” will be called:
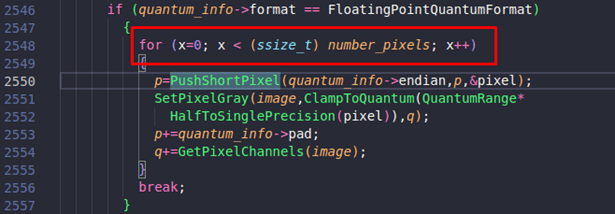
It is observed that “p” is being passed to “PushShortPixel” as pixels, and its value is increased by 2, as shown in lines 273 and 274:
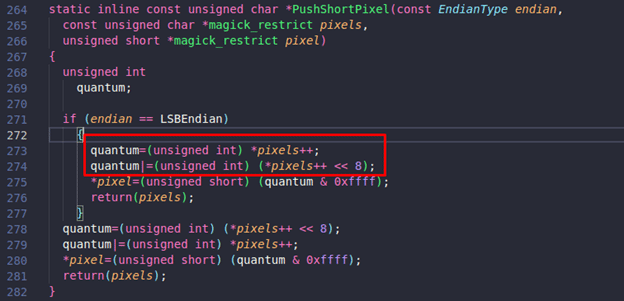
Now with every loop iteration, the value of “p” will be increased by 2, but there is no check inside “PushShortPixel” to verify if the value of “p” is more than the allocated memory. This will result in an off-by-one read, thus causing the crash.
The actual memory required here was 516 bytes, but the memory that was allocated was 264 bytes because the value of “extent” was not calculated properly. This was the root cause of this vulnerability.
- How was it fixed?
To fix this issue, extra checks have been added which properly calculates size of and extent which now considers “tile_size”,”stride” etc., and allocates 516 bytes of memory as shown below, thereby fixing this issue:
Conclusion:
ImageMagick is a popular software that is widely used for editing and manipulating images. A vulnerability like this can lead to crash-and-denial of service. Vehere’s security research wing, Moon Treader, will continue to fuzz various software and responsibly disclose such vulnerabilities to affected vendors. The team would like to acknowledge the efforts of the ImageMagick team for promptly patching the issue. The recommendation to the users is to keep their software up-to-date and apply the latest vendor patch whenever applicable.
References:
https://access.redhat.com/security/cve/cve-2023-3428
https://github.com/ImageMagick/ImageMagick/commit/a531d28e31309676ce8168c3b6dbbb5374b78790
