New Technology LAN Manager – A Look at NTLM Authentication
In our previous series of blogs, we delved deep into various Lateral Movement techniques, exploring topics such as user enumeration with the Security Accounts Manager (LSASS), remote service control via SCMR, and remote registry operations through the Windows Remote Registry Service. To get a better understanding of how an attacker would gain access to these privileged services, one needs to understand the way Windows authenticates users accessing a service or a share. In this blog, we will focus on New Technology LAN Manager, or NTLM, which is an authentication protocol employed by Windows to verify the credentials of a user account before allowing the account to access shares or services.
Windows New Technology LAN Manager:
Windows has all local user account passwords stored in the form of a one-way hash called the NTLM hash in its Security Accounts Manager (SAM) database; NTLM is a challenge-response authentication protocol. When a user tries to connect to a resource like a share or an MSRPC service, the user is presented with a challenge by the server hosting the resource. This challenge is an 8-byte random number generated by the server. When SMB, the underlying protocol in Windows, tries to access a share, it starts off by negotiating an SMB dialect. This is followed by a server challenge, as shown in the following screenshot.
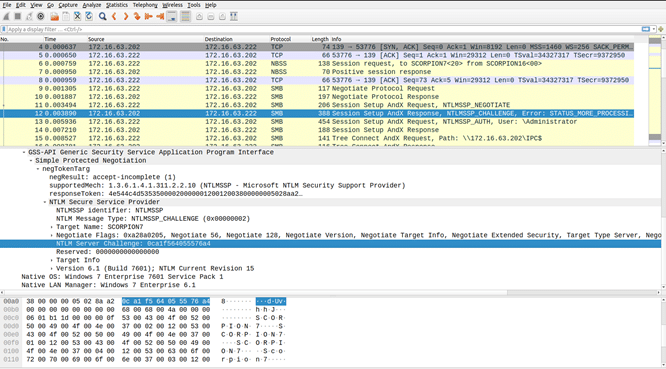
When a client attempts to access a resource, the server NTLM challenge is sent to the client. At the client’s end, it retrieves the NTLM hash of the user account’s password from its local SAM database. The client-side SMB then performs a computation using this NTLM password hash and the server’s challenge. This computation follows an open standard and can be implemented using various programming languages. The outcome of this computation, along with the user account’s name, is sent back to the server. This process is illustrated in the upcoming screenshot, displaying the client’s NTLM response and the user account name for accessing the resource.
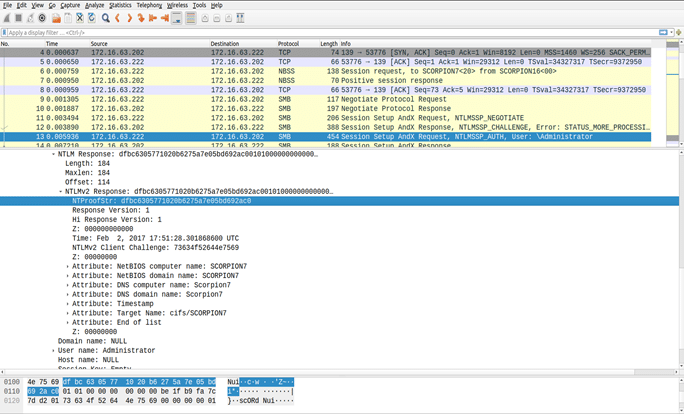
Upon receiving the client response, the server extracts the hash computed by the client and the user account name. It then retrieves the NTLM hash of the user account’s password from its local SAM database. The server applies the same NTLM computation, utilizing the challenge it sent and the NTLM hash from its SAM database. The result of this computation is compared with the NTLM response hash provided by the client. If these two hashes match, it indicates to the server that legitimate access to a resource is being invoked and that access is granted.
Weakness in NTLM:
Even though the user account password or its NTLM hash is never sent across the network, the NTLM protocol has an inherent flaw. If an attacker can gain access to a user account’s NTLM hash, the attacker can use this hash to compute the client-side response to a server’s challenge and get authenticated. Tools like Mimikatz allow an attacker or malware to have NTLM hashes extracted from the LSASS process, the Windows registry, the login screen, and several other locations. Libraries like impacket and modified versions of PsExec allow attackers to use NTLM hashes extracted from an infiltrated machine to access other machines in the network.
Vehere Network Detection and Response (NDR) Rules for Lateral Movement
In the previous sections, the NTLM authentication protocol was introduced, and its inherent security weakness was observed. Several lateral movement techniques, discussed in previous articles and to be discussed in upcoming ones, utilize this flaw in NTLM to gain access to a remote system using just NTLM hashes extracted by tools like mimikatz.
Vehere’s security research wing keeps these lateral movement rules updated to have complete coverage of the latest techniques employed by threat actors and malware.
In the next part of this series, we will learn about pass-the-hash attack, which leverages dumped NTLM credentials from a Windows machine to authenticate an attacker without needing to know the password.
