Introduction
In the ever-evolving landscape of cybersecurity, vulnerabilities continue to surface, posing risks to various software systems. One such notable vulnerability is the Command Injection Vulnerability CVE-2023-20887, which was discovered in VMware Aria Operations for Networks, a network monitoring tool.
In this blog post, we aim to provide an overview of this vulnerability, its potential impact, and recommendations for mitigating the associated risks.
Understanding VMware Aria Operations for Networks
VMware Aria Operations for Networks, formerly known as vRealize Network Insight, is a comprehensive network operations management tool. It is designed to provide visibility, analytics, and troubleshooting capabilities for complex network environments. By using this tool, organizations can optimize their network performance, ensure compliance, and enhance their security posture.
Detailed Overview of CVE-2023-20887
What is a Command Injection Vulnerability?
A command injection vulnerability occurs when an application improperly handles user input, allowing an attacker to execute arbitrary commands on the host system. This type of vulnerability is especially dangerous, as it can lead to unauthorized access, data exfiltration, and even full system compromise.
Technical Details and Exploitation Risks
CVE-2023-20887 is a command injection vulnerability discovered in VMware Aria Operations for Networks. Command injection vulnerabilities occur when an application constructs command strings using external input and executes them without proper sanitization or validation. This can allow an attacker to execute arbitrary commands on the host system, leading to unauthorized access, data exfiltration, or even complete system compromise.
The CVE-2023-20887 vulnerability is related to the improper handling of user input within certain API endpoints of VMware Aria Operations for Networks. When exploited, an attacker with network access to the management interface can execute arbitrary commands with elevated privileges on the underlying operating system.
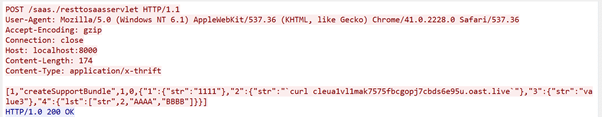
As can be seen from the above screenshot, a HTTP POST request is being sent to “resttosaasservlet” which contains Json data. If we look carefully, there is a parameter, which is “createSupportBundle” and then there is one “curl” command. Because of the vulnerability, this command will be executed.
Threat Severity:
According to Vehere’s threat severity scale, CVE-2023-20887 is classified as High. This classification is due to its potential for severe damage and ease of exploitation. The vulnerability is also listed in the CISA known vulnerabilities catalogue, highlighting that it is being exploited in the field.
Potential Impact
The vulnerability has been assigned a CVSS (Common Vulnerability Scoring System) score of 9.8. This high score underscores the potential for significant impact if the vulnerability is not promptly addressed.
Exploitation of CVE-2023-20887 can have severe consequences for affected systems and organizations, including:
- Unauthorized Access: Attackers can gain unauthorized access to sensitive information stored within the system.
- System Compromise: Exploiting this vulnerability can allow attackers to execute arbitrary commands, potentially leading to a complete system compromise.
- Data Exfiltration: Sensitive data can be exfiltrated, resulting in data breaches and potential legal and regulatory ramifications.
- Service Disruption: Malicious commands can disrupt network operations, leading to downtime and loss of productivity.
Detection, Mitigation Strategies and Best Practices
Vehere’s security research wing, Moon Treader, has created a rule to detect this malicious activity: “TI03177 VMware Aria Operations for Networks Command Injection CVE-2023-20887”
To mitigate the risks associated with CVE-2023-20887, VMware has released security patches and updates. Organizations using VMware Aria Operations for Networks should take the following steps:
- Apply Patches: Ensure that the latest security patches and updates provided by VMware are applied promptly. This is the most effective way to address the vulnerability.
- Network Segmentation: Limit network access to the management interface of VMware Aria Operations for Networks. Implement network segmentation and access controls to reduce the attack surface.
- Input Validation: Ensure that all user inputs are properly sanitized and validated before being processed by the application. This can help prevent command injection and similar vulnerabilities.
- Monitor Systems: Continuously monitor systems for any signs of unusual activity or attempted exploitation. Implement intrusion detection and prevention systems to enhance security.
- Security Best Practices: Follow security best practices, such as least privilege principles, regular security assessments, and user education to further strengthen your security posture.
Vehere AI Network Security:
A 5-in-1 unified platform that acts as a “Second line of Defense” to protect your corporate network from the most advanced cyberthreats. It combines lossless packet capture with advanced threat hunting and AI-driven analytics to provide real-time visibility and rapid response. By proactively identifying and neutralizing threats, we empower organizations to safeguard their critical assets and maintain business continuity.
Conclusion and Final Recommendations
CVE-2023-20887 is a command injection vulnerability in VMware Aria Operations for Networks that underscores the importance of proactive security measures. By staying informed about such vulnerabilities and promptly applying patches, organizations can significantly reduce the risk of exploitation and protect their valuable assets. As always, maintaining a robust security posture requires a combination of technical solutions, best practices, and ongoing vigilance. Moon Treader’s ongoing research and development efforts ensure that detection capabilities are always up-to-date, enhancing the security posture of Vehere’s customers.
FAQs
Q1: What is CVE-2023-20887?
A1: CVE-2023-20887 is a command injection vulnerability in VMware Aria Operations for Networks that allows attackers to execute arbitrary commands on the host system.
Q2: How can CVE-2023-20887 be exploited?
A2: The vulnerability can be exploited by sending crafted HTTP POST requests to specific API endpoints, allowing the execution of malicious commands with elevated privileges.
Q3: What are the consequences of not patching CVE-2023-20887?
A3: Failure to patch this vulnerability can result in unauthorized access, system compromise, data breaches, and significant service disruptions.
Q4: How can organizations protect themselves from this vulnerability?
A4: Organizations should apply the latest patches, implement network segmentation, validate user inputs, and continuously monitor for suspicious activities.
Q5: Is there a detection tool for CVE-2023-20887?
A5: Yes, Vehere’s Moon Treader has developed a detection rule to identify activities related to this vulnerability, enhancing security monitoring capabilities.
Q6: Where can I find the latest updates on this vulnerability?
A6: For the latest information, refer to the VMware Security Advisory.
References:
https://www.vmware.com/security/advisories/VMSA-2023-0012.html