If you’re running Atlassian Confluence Server or Data Center, you could be facing a major security risk. Recently, a critical vulnerability (CVE-2023-22515) was discovered that, if exploited, could allow attackers to create administrative accounts and take full control of your system. In this post, we’ll break down what CVE-2023-22515 is, how it works, and most importantly, how you can protect your Confluence instance.
What is CVE-2023-22515, and Why Should You Care?
Let’s start with the basics. CVE-2023-22515 is a Remote Code Execution (RCE) vulnerability affecting on-premises installations of Confluence Data Center and Server. When exploited, it allows attackers to remotely create unauthorized administrative accounts, essentially giving them full control of your Confluence environment.
Imagine the damage that could be done with administrative access—attackers could steal sensitive information, install malicious software, or even take your entire system offline. For businesses relying on Confluence for internal documentation, project management, or collaboration, the consequences could be devastating.
How Does the CVE-2023-22515 Exploit Work?
So, how exactly does this vulnerability work? An attacker sends a malicious HTTP POST request to the server using the endpoint /setup/setupadministrator.action. The attack is successful because the system bypasses security checks with a special ‘X-Atlassian-Token: no-check’ header, allowing the attacker to create a new admin-level user account.
Once that admin account is created, it’s game over. The attacker can now access your entire system, steal data, or even use your compromised server to launch attacks on other parts of your network.
The following screenshot describes the creation of the user:
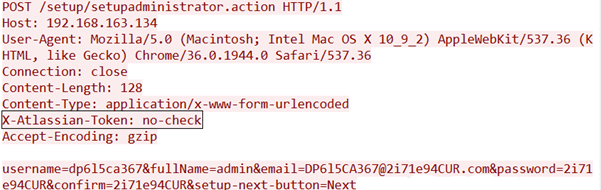
In the above screenshot, a POST request is sent as “/setup/setupadministrator.action”. Additionally, the ‘X-Atlassian-Token: no-check’ header has been added to bypass security checks. Once a hacker successfully exploits this vulnerability, they can create an administrator account with full access to your system.
How Severe is CVE-2023-22515?
This is not just a run-of-the-mill security issue. CVE-2023-22515 is classified as critical by experts, and it’s included in the CISA’s Known Exploited Vulnerabilities list, which means it has been actively exploited in the wild. If your system is compromised, you could be looking at a full-blown security disaster.
Is Your Confluence Installation Vulnerable?
If you’re using any Confluence Data Center or Server version prior to 8.3.3, 8.4.3, or 8.5.2, your system is vulnerable to this attack. It’s crucial to check your version and take immediate action to protect your business.
How to Protect Your Confluence System
1. Upgrade to a Secure Version Immediately
The fastest and most effective way to protect your system is to upgrade to a secure version of Confluence. Atlassian has released patches for this vulnerability in the following versions:
- 8.3.3
- 8.4.3
- 8.5.2 (or newer)
2. Implement Workarounds if You Can’t Upgrade Right Away
Sometimes, upgrading right away isn’t possible due to internal processes or dependencies. If that’s the case, Atlassian has provided workarounds to reduce your risk of exploitation. One workaround involves restricting access to specific setup files that the vulnerability targets.
3. Monitor Your System with Advanced Threat Detection
While upgrading your system is the most crucial step, having ongoing monitoring in place is just as important. Tools like Vehere AI Network Security provide real-time visibility into your network and can detect suspicious activity, such as unauthorized account creation. This tool serves as a powerful second line of defense, helping to identify threats before they cause significant damage.
What’s Vehere AI Network Security?
Vehere AI Network Security is a comprehensive security platform that helps you detect and respond to advanced cyber threats. By utilizing AI-driven analytics and lossless packet capture, it can spot anomalies in real-time, ensuring you stay ahead of attackers.
With its TI06162 rule specifically designed to catch CVE-2023-22515 exploits, it acts as an essential tool to guard against vulnerabilities in Confluence Data Center and Server.
The Importance of Patch Management
One of the most important lessons from CVE-2023-22515 is the need for a robust patch management strategy. Cyber threats evolve rapidly, and new vulnerabilities are discovered all the time. Keeping your software up to date is one of the easiest and most effective ways to safeguard your systems.
Regular updates ensure that known vulnerabilities, like CVE-2023-22515, are patched, keeping attackers at bay. Automating this process or scheduling regular checks can help minimize the chances of missing crucial updates.
Stay Ahead of Cyber Threats
The cyberthreat landscape is constantly changing, but by staying informed, you can reduce your risk significantly. We strongly recommend the following best practices to protect your Confluence instance:
- Upgrade to the latest versions of all your software, especially Confluence.
- Use advanced security solutions like Vehere AI to monitor your network in real-time.
- Stay updated on newly discovered vulnerabilities and apply patches as soon as possible.
By taking these steps, you’ll be well on your way to securing your system and minimizing the risk of future attacks.
FAQs on CVE-2023-22515
1. What makes CVE-2023-22515 so dangerous?
CVE-2023-22515 allows attackers to remotely create administrative accounts, giving them full control of your Confluence system, including access to sensitive data and the ability to launch further attacks.
2. How can I tell if my Confluence system is vulnerable?
If you’re using Confluence Data Center or Server versions prior to 8.3.3, 8.4.3, or 8.5.2, your system is at risk.
3. What’s the quickest way to fix this vulnerability?
The best way to protect your system is to upgrade to a patched version immediately. If that’s not possible, follow the workarounds provided by Atlassian.
4. Can Vehere AI help protect my system?
Yes, Vehere AI’s Network Security platform provides real-time monitoring and advanced threat detection, helping to identify and neutralize exploits like CVE-2023-22515.
5. Why is it important to patch regularly?
Regular patching closes known vulnerabilities, like CVE-2023-22515, before attackers can exploit them. This is a key part of any solid security strategy.6. Where can I learn more about this vulnerability?
For more details, visit Atlassian’s official security advisory on CVE-2023-22515: Atlassian Security Advisory.
By ensuring your Confluence environment is secure, you’re protecting not only your data but the overall integrity of your business operations. Take action today to prevent CVE-2023-22515 from becoming a real threat to your company.