Introduction
The fight against cyber threats never stops, and Remote Access Trojans (RATs) like AsyncRAT continue to push the boundaries of digital security challenges. With its ability to infiltrate systems undetected and execute a range of malicious tasks, AsyncRAT poses a significant risk to businesses and individuals alike.
Thankfully, correlation rules—smart tools that identify suspicious activity patterns—are helping to level the playing field. In this article, we’ll break down AsyncRAT, explore how correlation rules work, and share actionable strategies to safeguard your systems.
What is AsyncRAT and Why Should You Care?
AsyncRAT is more than just a clever acronym—it’s a cybercriminal’s best friend. This Remote Access Trojan offers hackers a full suite of tools to spy on, control, and exploit a victim’s system. Some of its most alarming features include:
- Stealing Credentials: From passwords to personal data, AsyncRAT thrives on sensitive information.
- Keylogging: It records everything you type, exposing your activities.
- Remote Commands: Attackers can run harmful scripts or programs.
- Stealthy Surveillance: Monitoring your system without leaving any obvious traces.
If you’ve ever received a suspicious email, clicked a shady link, or downloaded an attachment from an unknown source, you’ve likely encountered the methods AsyncRAT attackers use to spread their malware.
Why AsyncRAT Remains a Formidable Threat
AsyncRAT is designed to stay ahead of traditional antivirus solutions. Here’s why:
- It’s Sneaky: AsyncRAT uses encrypted communication to avoid detection.
- It’s Customizable: Hackers can modify it to meet specific objectives.
- It’s Persistent: Once inside your system, it works quietly in the background, gathering data or setting up further attacks.
The question isn’t if AsyncRAT will evolve—it’s how fast. That’s why staying proactive with smart tools like correlation rules is vital.
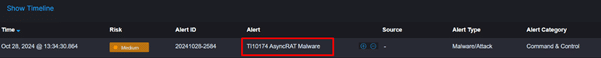
How Correlation Rules Detect AsyncRAT
Correlation rules are like your cybersecurity team’s best detective. They analyze activity patterns in your systems, flagging anything unusual. Here are three essential rules to keep AsyncRAT in check:
1. Monitoring Non-Standard HTTP Ports
AsyncRAT often communicates over unusual HTTP ports to avoid detection.
- Why it Matters: Most internet traffic uses standard ports (like 80 and 443). Anything else is a red flag.
- How to Detect: Set up rules to monitor HTTP traffic on unconventional ports and trigger alerts when detected.
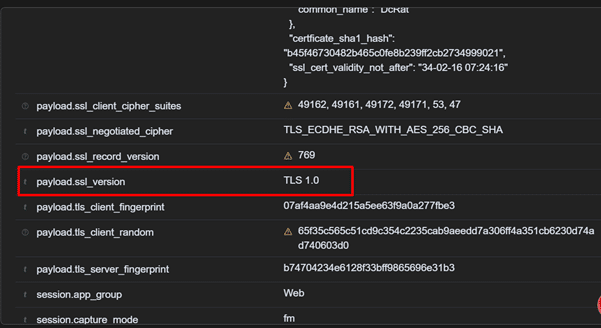
2. Identifying Outdated TLS Protocols
AsyncRAT likes to exploit outdated encryption methods, like TLS 1.0 or 1.1, which are less secure.
- Why it Matters: Modern protocols (TLS 1.2 or higher) are far safer. Detecting older versions can reveal hidden threats.
- How to Detect: Track encrypted traffic and alert on deprecated protocols.
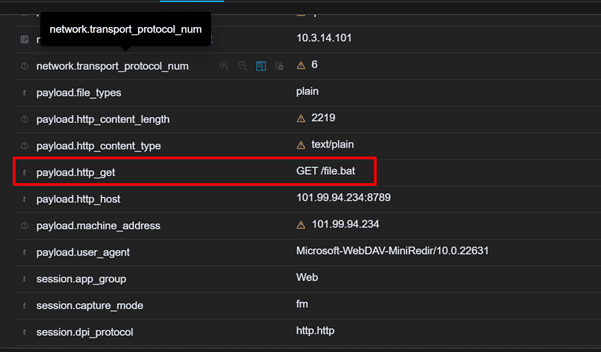
3. Spotting Suspicious File Downloads
Attackers often use Batch (BAT) files to deploy AsyncRAT on victim systems.
- Why it Matters: BAT files often accompany malware in phishing emails or compromised downloads.
- How to Detect: Monitor for unexpected BAT file downloads from untrusted sources.
Old TLS version
BAT file download
AsyncRAT Malware alert
Vehere’s Multilayered Defense Against AsyncRAT
Vehere’s AI Network Security (a unified solution of Network Detection & Response and Network Forensics) has adopted a multilayered strategy to tackle AsyncRAT, combining:
- Real-Time Alerts: Instant notifications of suspicious activities.
- Comprehensive Detection: Correlation rules that track AsyncRAT behavior at every stage.
- Ongoing Updates: Rules are continually refined to counter evolving threats.
This proactive approach gives organizations a fighting chance against AsyncRAT’s sophisticated techniques.
How to Stay Ahead of AsyncRAT Threats
While AsyncRAT is complex, defending against it doesn’t have to be. Here are some practical tips:
- Invest in Advanced Monitoring Tools: Solutions with correlation rule capabilities offer a significant edge.
- Educate Your Team: Many AsyncRAT attacks start with phishing emails. Train your employees to spot red flags.
- Update Regularly: Outdated software is an easy target. Keep systems, protocols, and detection rules up to date.
- Incorporate Threat Intelligence: Real-world insights help tailor detection rules to current trends.
The Big Picture: Why Correlation Rules Are a Must-Have
Let’s face it—AsyncRAT is here to stay, and it’s only getting more advanced. But with well-tuned correlation rules, you’re not just detecting threats; you’re also learning more about your system’s vulnerabilities.
- Correlation rules shine a light on hidden malware behaviors.
- They provide critical insights into your network’s overall health.
- They evolve with your defenses, ensuring you’re ready for the next wave of cyber threats.
Conclusion
AsyncRAT may be a crafty adversary, but it’s far from unbeatable. By adopting correlation rules, educating your team, and continuously adapting your defenses, you can stay one step ahead of this and other advanced threats. The key is proactive detection and response—because in cybersecurity, waiting for a breach is never an option.
FAQs
- What makes AsyncRAT so dangerous?
Its ability to operate silently, steal sensitive data, and allow remote control of a system makes AsyncRAT a powerful tool for attackers. - How do correlation rules work?
Correlation rules analyze patterns in system activities and flag anything unusual, like non-standard HTTP ports or outdated TLS protocols. - Why are outdated TLS protocols a risk?
Older TLS versions lack robust encryption and are easily exploited by malware like AsyncRAT to mask its activities. - How does Vehere AI Network Security improve AsyncRAT detection?
Vehere AI Network Security uses real-time alerts, advanced correlation rules, and ongoing updates to detect AsyncRAT at various stages of its attack. - Can AsyncRAT attacks be prevented?
While prevention isn’t always possible, tools like correlation rules and employee training can significantly reduce the risk of an attack. - How often should detection rules be updated?
Detection rules should be updated regularly to keep pace with evolving threats and incorporate real-world intelligence.
