Understanding the Shift in Cyberattack Tactics
The 2025 Verizon Data Breach Investigations Report (DBIR) reveals a notable change in the ever-changing environment of cybersecurity threats: vulnerability exploitation has become a more common first point of entry for breaches.
Unpatched software issues, especially in edge devices and virtual private networks (VPNs), are rapidly opening the door to numerous breaches, which have hitherto been dominated by phishing attempts and credential exploitation.
To strengthen their defenses, organizations need to comprehend this change and adjust accordingly.
Vulnerability Exploitation Now Drives More Breaches
According to the DBIR, vulnerability exploitation caused 20% of breaches in 2025, a staggering 34% increase over the previous year. This makes it the fastest-growing initial access vector.
- Phishing remains relatively stable at 15%
- Credential misuse still leads slightly at 22% but is declining
- Exploitation of edge devices and VPNs jumped from 3% to 22%, an almost eightfold increase
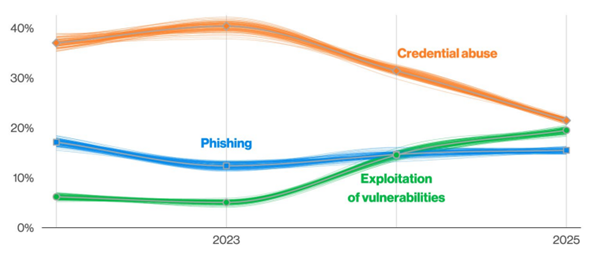
Evolving Entry Points in Data Breaches (Non-Error, Non-Misuse)
(Source: Verizon)
This rapid rise highlights a change in attacker strategy, prioritizing automation and speed over traditional, user-dependent methods.
The Role of Edge Devices and VPNs in the Breach Spike
The discovery of flaws in gadgets that connect directly to the internet is mostly to blame for this increase. Even though companies rushed to fix these flaws, according to the DBIR,
- Only 54% of vulnerabilities were completely fixed in a year.
- The median time to patch was a startling 32 days
Giving attackers a large window of opportunity (Verizon, 2025).
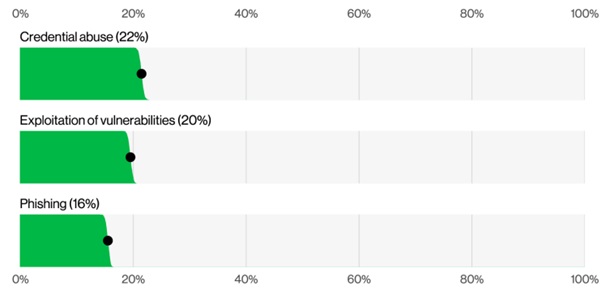
Initial Access Vectors in Breaches Excluding Error and Misuse
(Source: Verizon)
According to these results, routers, firewalls, VPN gateways, and other edge technologies are now considered to be perimeter equipment.
Although edge devices are now essential to business operations due to the growth of remote work and cloud services, they are frequently not properly updated or secured. Attackers have changed their focus in response to this opportunity.
Espionage-Driven Breaches Highlight Strategic Risk
A troubling relationship between vulnerability exploitation and more general threat trends is also highlighted by this development. 70% of breaches with espionage motivations used vulnerability exploitation to get first access. This highlights the strategic importance of unpatched systems to nation-state actors and the dangers that go beyond simple monetary losses (Verizon, 2025).
Third-Party and SaaS Vulnerabilities Are Expanding the Attack Surface
Third-party involvement in breaches has increased to 30%, which makes issues even more complicated. Software or service providers are often the source of breaches, as their flaws or setups serve as the attacker’s point of access.

Percentage of third-party involvement in breaches
(Source: Verizon)
Incidents involving Snowflake and other SaaS platforms, where attackers took advantage of lax or unenforced multifactor authentication (MFA) controls—which are frequently made possible by the first compromise of credentials or tokens left unsecured—significantly demonstrated this dynamic.
Secrets in Public Repositories Extend Exploitation Opportunities
Additionally, the DBIR highlights the tardy cleanup of compromised passwords and secrets in open repositories such as GitHub. An unsettling 94 days was the median period to fix secrets that were exposed.
The initial exploitation risk might be increased during that period if attackers used exposed API keys or credentials to gain access to sensitive systems.
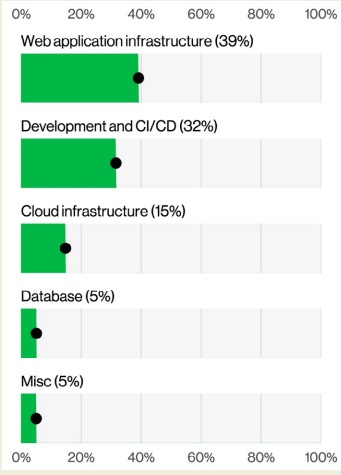
Top categories of exposed secrets in public git repos
(Source: Verizon)
Breaches Are Becoming Less Human-Driven and More Automated
A larger trend is indicated by the move toward exploitation as a first access method: cyberattacks are becoming less dependent on human error and more automated and opportunistic.
Even if phishing tactics continue to claim a large number of victims, attackers are increasingly searching for weak systems in large quantities, automating the exploitation process, and deploying malware or ransomware in a matter of minutes.
Traditional Defenses Fall Short Against Exploitation
Additionally, this change calls into question traditional defensive stances. Even while it is still very important, traditional security awareness training is unable to stop an attack that takes advantage of an unpatched VPN device.
Similar to this, lateral movement may be detected by endpoint detection and response (EDR) systems, but frequently only after initial access has been obtained.
Vehere’s Key Recommendations to Stop Vulnerability Exploits
Vehere AI Network Security suggests organizations must adopt more proactive vulnerability management strategies. These include:
- Deploy Network Detection and Response (NDR): Consider deploying Network Detection and Response (NDR) solutions as a best practice to continuously monitor network traffic, detect suspicious behavior or anomalies early, and enable rapid, automated response to potential threats
- Prioritization of Edge Device Security: Patching and monitoring of edge devices must be given top priority due to their vital role and exposure. Strict network segmentation should be used by organizations to isolate these devices wherever feasible.
- Exposure Reduction: Reduce the quantity of devices that are in contact with the internet. Enable strong authentication techniques like MFA and make sure setups are hardened if exposure is required.
- Enhancements to Patch Management: Simplify the procedures for patch deployment and vulnerability scanning. Reduce the patch window by automating where you can, and prioritize high-impact vulnerabilities first.
- Third-Party Risk Management: Make sure that vendors and third-party providers adhere to strict security guidelines and undergo audits. Recognize their incident response skills and patching practices.
- Enforce safe credential management procedures, such as regular credential rotation, robust authentication, and prompt remediation of secrets that have been leaked.
Conclusion: Evolve Defenses to Match Exploitation Trends
In conclusion, there is a clear warning regarding the growing role of exploitation as an initial breach vector. Companies need to protect their technical environments from direct abuse in addition to defending against social engineering. Defenders must adjust as the opponents have.
Organizations are left vulnerable in a threat landscape that is always changing and growing more vicious if security procedures are not adjusted to reflect this change.
Stay ahead of emerging threats. Explore Vehere AI Network Security platform for proactive vulnerability management.