- We’ll be at RSA Conference 2026, Moscone Center, San Francisco | 23rd - 26th March, 2026 | N-6473
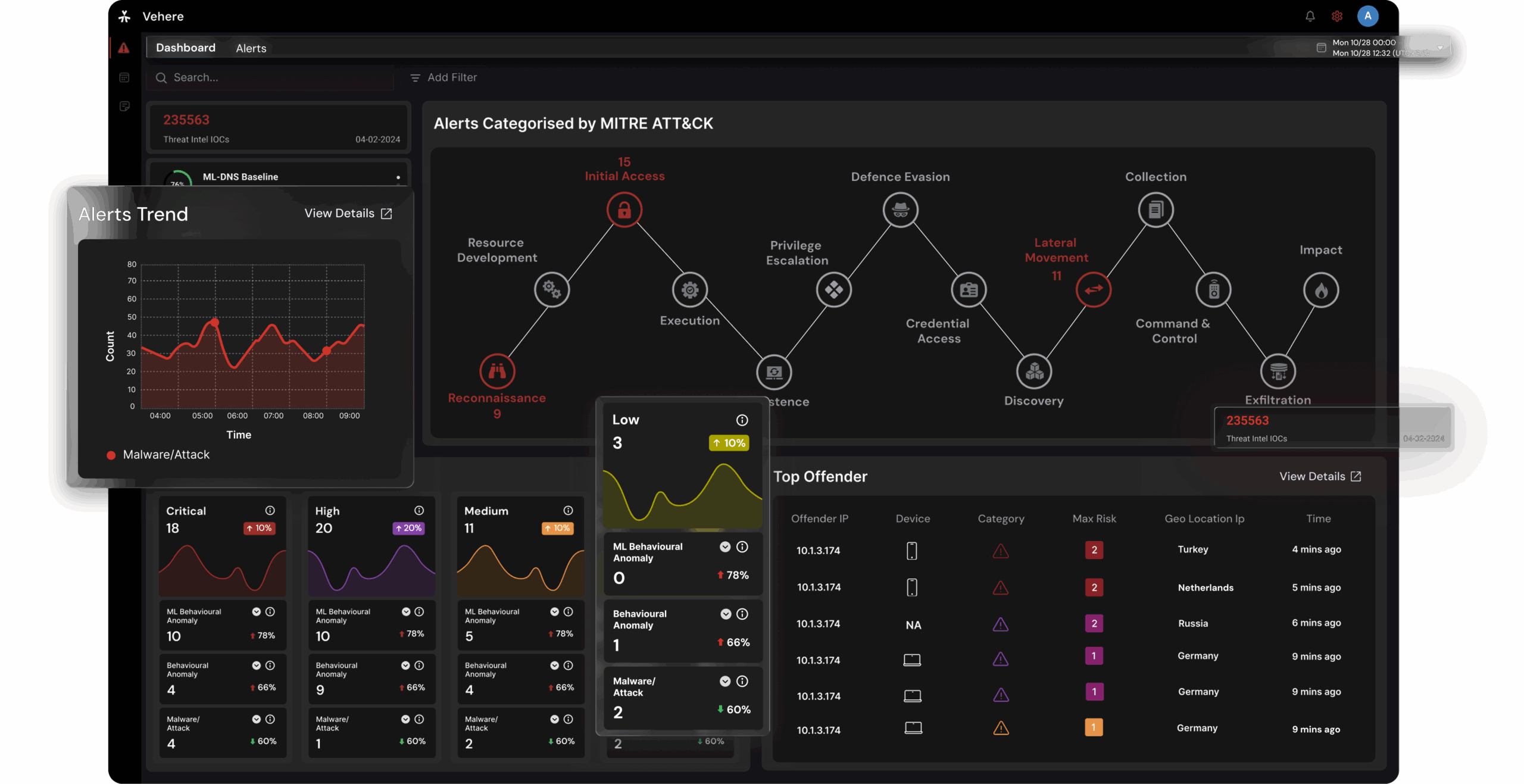










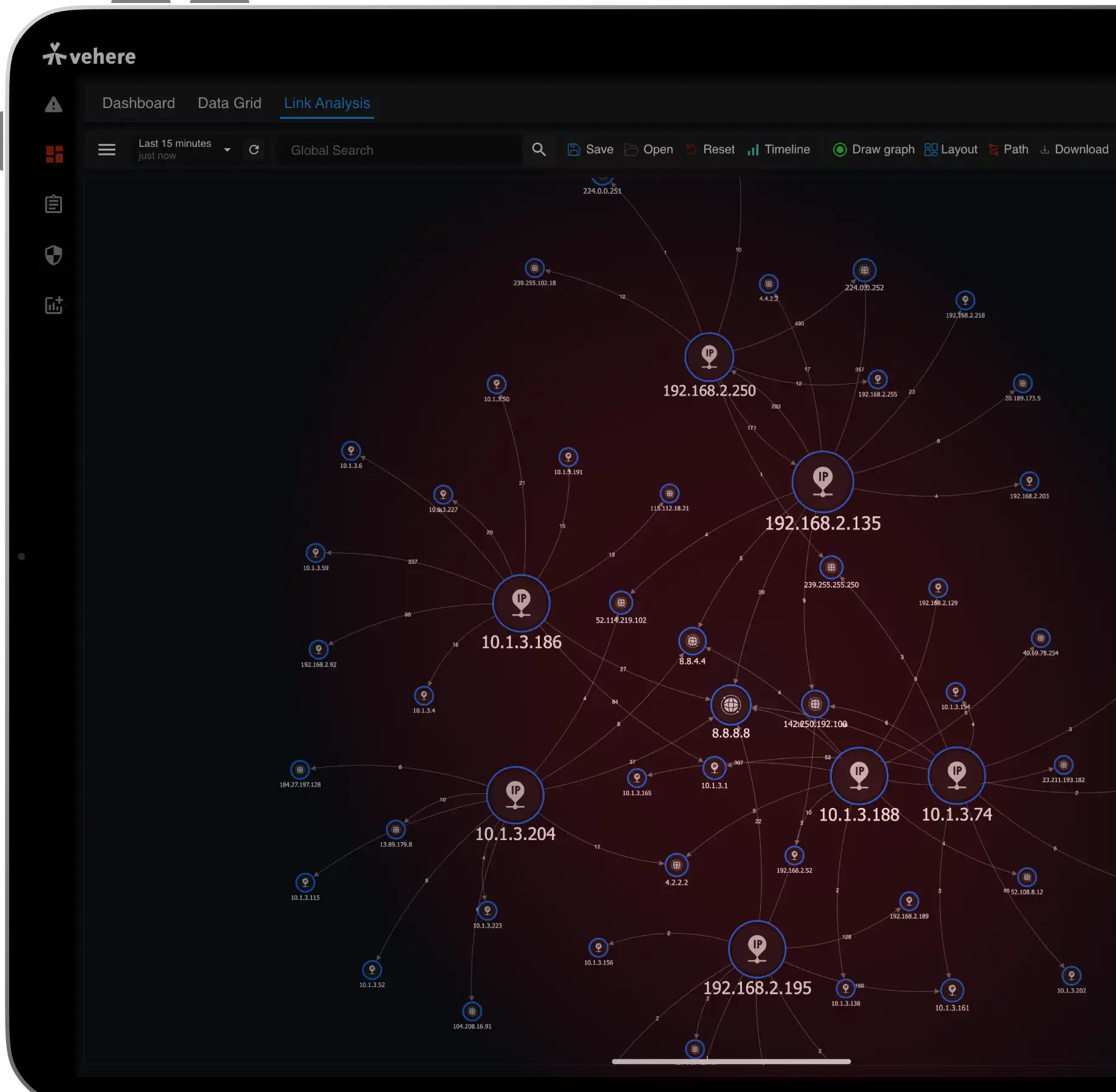
Our cyber defense software, battle-tested by the world’s toughest defense and intelligence agencies, uses advanced hacker models that predicts and neutralizes the most sophisticated threats before they strike.
Battle-tested NDR built for modern threats and mission-critical environments
100% Lossless packet capture and forensic investigation for post-incident analysis and legal evidence
Passive, packet-based interception across mobile, fixed, satellite and IP networks



See everything, everywhere, capture flow and raw packets at wire speed, inspect traffic across 5000+ protocols, and unlock instant forensic insights for every device and conversation.

“Vehere fosters a positive work culture with vehere approachable management and a dynamic work environment.”

Government

“The overall experience with the product has been satisfactory, with good support from the technical and support teams. They are prudent to adapt and vehere customize the product as per the customer’s requirement.”

IT Security and Risk Management, Banking

“We are using Vehere NDR for one of our Banking customers, the product has more enhanced features vehere to identify the anomalies over the network with the help of Al / ML based policy fine-tuning.”

IT Services
Moon Treader, Vehere’s go-to security research wing, actively investigates and monitors the latest developments in the cyberthreat landscape and upgrades the detection capabilities to improve the security posture of Vehere’s customers.
Complete visibility, real-time threat detection, proactive protection, and intelligent response
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |