High speed and real-time passive interception platforms for lossless data extractions with next-gen DPI probe, delivering effective intelligence and security.
360 degree view of adversaries by providing a unified view of all intercepted data on a single interface.
Capabilities powered by AI such as Audio Analysis, Text Capabilities, Predictive Analysis, Pattern Recognition and more.
Vehere’s technology enables collection and analysis of data from diverse communication network sources, including telephone calls, mobile data, and Internet-based services such as email, voice over-IP, instant messaging, and others.
Vehere also delivers National and Cross-border Cyber Vigilance for detection and containment of post-breach activities. It ensures full visibility with lossless packet capture, full digital forensics, next-gen file analysis, AI-powered breach detection and threat hunting.
Vehere strengthens national security without compromising constitutional privacy protections, embodying the core principle of ‘Protection with Privacy’.
AI-powered intelligence collection system enhanced with Natural Language Processing, featuring capabilities such as spam filtering, language detection, speaker recognition, and many more.
Manages and monitors millions of subjects effectively.
Ingestion and assimilation of diverse external data sources, utilizing a robust ETL (Extract, Transform, Load) engine.
Architecture designed for 100+ Gbps & full duplex scalability and cost-efficiency.
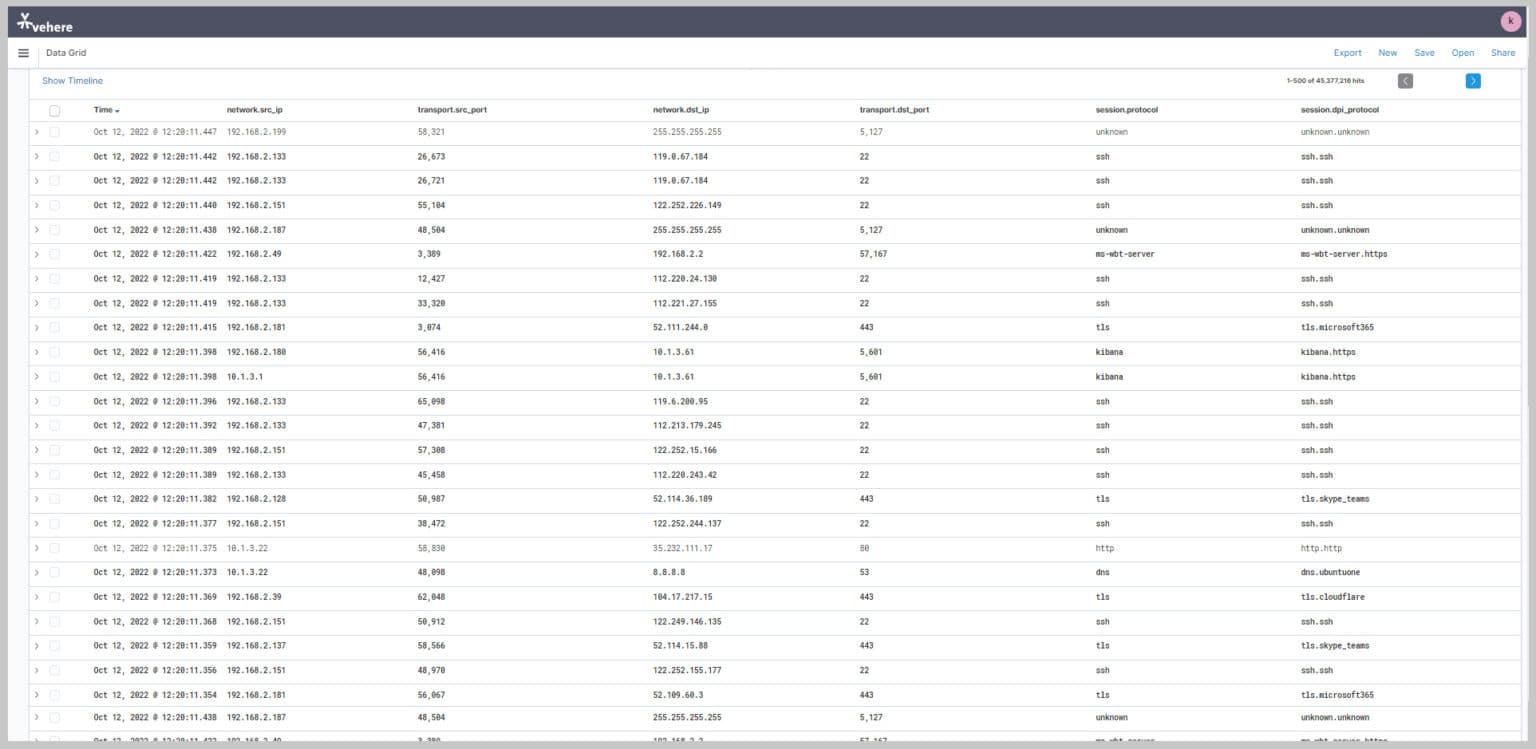
Comprehensive text search capabilities for extensive intelligence gathering.
Examine and assess suspect activity via detailed metadata analysis.
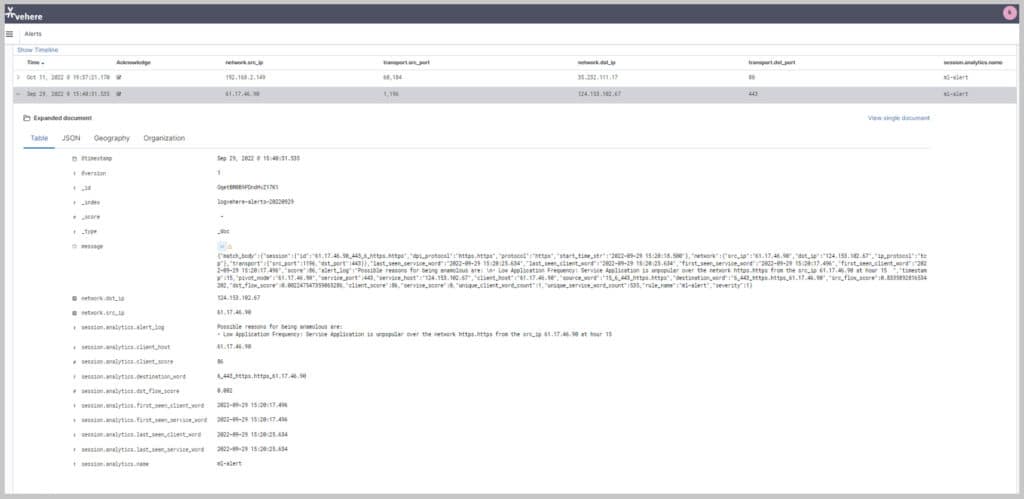
Machine learning and rule-based alert triggering system
• Reliable and continuous collection across a wide range of communication network sources and technologies
• Automatically focus on the most relevant sources for efficient coverage management and resource allocation
• AI-powered analytics to identify relations, interests, activities, patterns and abnormalities
• Detect and highlight suspicious indicators, unique insights and new patterns
Network Intelligence Analytics
Network Intelligence Analytics help protect nation and its citizens by collecting mass, wide and target data from diverse communication network sources.
Fiber Data Analytics
Fiber Data Analytics analyzes high-speed data streams from submarine and terrestrial cables to identify and track nation state for improving situation awareness.
Cyber Vigilance
Massive scale NDR-NF for national critical infrastructure that detects and contains post-breach activities like ransomware, APTs, insider threats or lateral movements using AI/ML and heuristic behaviour analytics.
Lawful Interception
A state-of-the-art monitoring solution for LEAs to help fulfil their legal obligations to intercept calls and data while maintaining maximum privacy and protection.
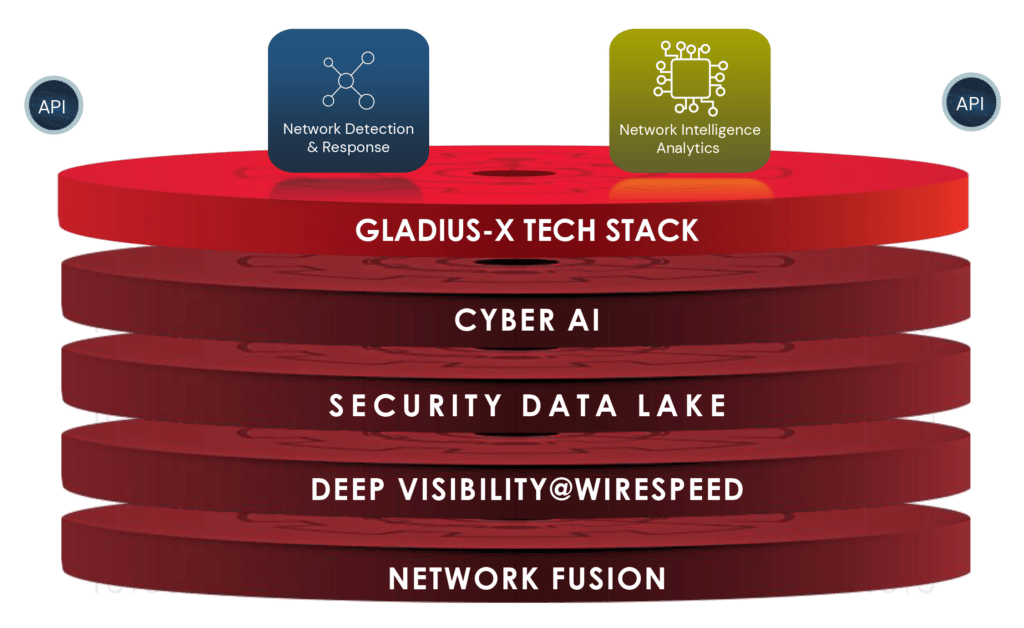
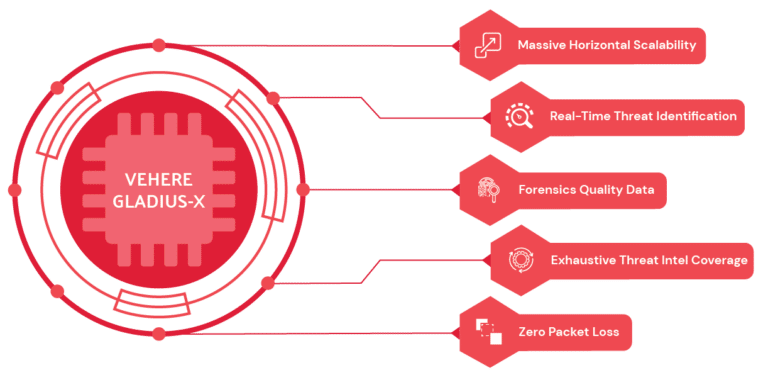
The "Gladius-X", a Vehere’s exclusive intellectual and proprietary tech-stack for fighting against deadliest threat actors and dreadful anomalies.
AI-powered Language identification (supporting 99 languages) aids in transcription and translation in Audio and Speech to Text Conversions. Allows analysts to efficiently process recorded audio files.
Analysis using available senses such as relying on metadata, behavior models and other signals. Analysis of encrypted domain to extract SSL certificates. Auto-profiling of encrypted traffic metadata
• Manual inspection of content is time-consuming and often error-prone.
• Without opening the content (that may actually be weaponized), IntelliWorker enable discovery across many thousands of documents to identify extent of leak of sensitive information in communication channel.
Target movement analysis and geofencing by harnessing the power of a 16-layer street view offline map.
Capability to visualize complex networks with 6-layered graph analysis and connect the dots so that nothing remains hidden .
Advanced metadata analytics tool to streamline the process of examining and interpreting metadata associated with digital files, documents, or datasets, delivering valuable insights and information.
• Encryption is a challenge for LEAs. Even the content may be encrypted.
• Vehere's NI enables analysis using statistical techniques enabling identification of origins.
• Special fingerprinting techniques enable identification of device and owner.
| Cookie | Duration | Description |
|---|---|---|
| cookielawinfo-checbox-analytics | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Analytics". |
| cookielawinfo-checbox-functional | 11 months | The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". |
| cookielawinfo-checbox-others | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Other. |
| cookielawinfo-checkbox-necessary | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookies is used to store the user consent for the cookies in the category "Necessary". |
| cookielawinfo-checkbox-performance | 11 months | This cookie is set by GDPR Cookie Consent plugin. The cookie is used to store the user consent for the cookies in the category "Performance". |
| viewed_cookie_policy | 11 months | The cookie is set by the GDPR Cookie Consent plugin and is used to store whether or not user has consented to the use of cookies. It does not store any personal data. |