
- Products >
-
<Back
- Solutions >
-
<Back
- Industries
-
<Back
Industries
- Company >
-
<Back
- Learn >
-
<Back
- Contact Us
-
<Back
Contact Us
AI Network Security
A 5-in-1 unified platform that is designed to protect your network from the most advanced cyber threats.
Wirespeed Visibility
Vehere's AI Network Security provides Wirespeed Visibility and Analysis from Layer 3 to Layer 7 leveraging advance AI/ML to provide real-time actionable alerts. MOVE BEYOND LOGS AND ENDPOINT SECURITY!
Real-Time Anomaly Detection
Location and device agnostic user and application profiling for improved visibility, behavior modelling and eventually resulting in better anomaly detection. Automated port agnostic protocol detection of thousands of protocols leading to Accurate application detection and response
Intelligent Response
Vehere's AI Network Security provides full context and one-click investigation workflows for every detection. Leverages artificial intelligence to immediately terminate harmful connections and contain network threats.
Vehere’s cutting-edge AI Network Security is a unified solution of Network Detection and Response (NDR) and Network Forensics (NF). It helps strengthen the security posture of enterprises by using machine learning, rule-based techniques and advanced analytics.
Vehere NDR detects suspicious activities in encrypted and non-encrypted traffic that conventional security tools are missing out on, and Vehere NF supports investigation and analysis of the root cause of network leakage, data theft, and suspicious network traffic.
Vehere AI Network Security helps enterprises secure their networks through real-time detection, threat hunting and comprehensive forensics.
Lossless packet monitoring of datacenter and branches ensures zero blind spots
Real-time threat detection to understand and be aware of what is happening in your network instantly.
Consumption of millions of Indicators of Compromise (IOCs) and Indicators of Attack (IOAs).
One-click evidence for incident response to investigate events in detail, swiftly, and effectively.
Advanced Forensics and Threat Hunting is a long term repository and powerful tools that enable analysts to investigate events in detail quickly and effectively, using evidence found in the original packets and files recorded from the network.
Security Initiatives
Protect your business from advanced threats with Vehere AI Network Security
Network Detection & Response
Protect your business by implementing Vehere’s AI-powered Network Detection & Response solution to identify any suspicious activity within the network.
Network Forensics
Detect the root cause of network leakage, data theft and suspicious network traffic with Advanced Network Forensics.
Mitigate Ransomware
Apprehend ransomware attacks by leveraging real-time detection of anomalies within the network and use this as an advantage to mitigate such ploys by malicious actors.
Zero Trust
Enterprises are moving away from traditional security approaches for fighting sophisticated network attacks. Enhance Zero Trust architecture to verify each entity seeking access to networks.
Cloud Security
Detect attacks across cloud infrastructure and services to stop compromises due to misconfiguration, credential theft and supply chain from turning into breaches.
IoT Security
Digitalization has augmented the use of IoT devices which has expanded the enterprise attack surface. Reinforce IoT security with real-time threat detection, advanced analytics and swift response.
Zero Trust
Enterprises are moving away from traditional security approaches for fighting sophisticated network attacks. Enhance Zero Trust architecture to verify each entity seeking access to networks.
Mitigate Ransomware
Apprehend ransomware attacks by leveraging real-time detection of anomalies within the network and use this as an advantage to mitigate such ploys by malicious actors.
IoT Security
Digitalization has augmented the use of IoT devices which has expanded the enterprise attack surface. Reinforce IoT security with real-time threat detection, advanced analytics and swift response.
Cloud Security
Detect attacks across cloud infrastructure and services to stop compromises due to misconfiguration, credential theft and supply chain from turning into breaches.
Network Forensics
Detect the root cause of network leakage, data theft and suspicious network traffic with Advanced Network Forensics.
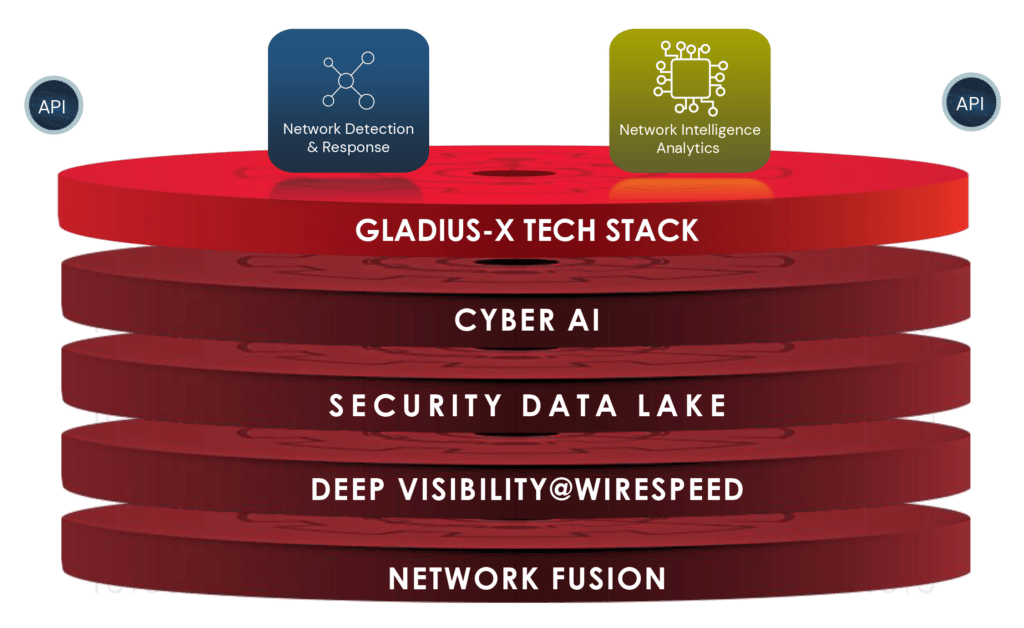
Gladius-X: Vehere's Tech-Stack
'Gladius-X' is Vehere’s exclusive intellectual and proprietary tech-stack for fighting against deadliest threat actors and dreadful anomalies.
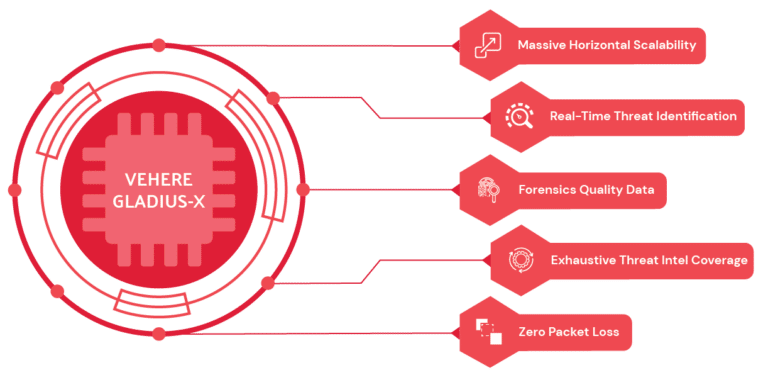
Gladius-X Differentiators
Security Use Cases
Detecting Alarming Activities on Network
The longer an attack on a network remains unknown, the more damaging it can be. Vehere AI Network Security is able to quickly show the top alarming activities on a network. This allows for quick investigation and mitigation of potential attacks. The solution prioritizes the threats to decrease Mean Time to Resolution (MTTR).
Investigating Hosts Using the Most Bandwidth
Organizations need to identify hosts consuming the most bandwidth across the whole network in a business unit or at a specific site. Vehere's AI Network Security Explore module enables users to determine how much bandwidth a host, a host group, or a particular site is consuming. This feature also shows the most used applications or services in a network.
Using Report Module for Performance Analysis
The Report module is essentially used in producing reports comprising the most relevant alarms, events, and activities for a user or team of network operators. This feature allows for report templates to be customized, fitting the requirements of multiple teams, and enabling them to use the detections and insights received more effectively.
Detecting Lateral Movement
Once an attack bypasses the perimeter, it can move through a network laterally, which is a characteristic of an Advanced Persistent Threat (APT). It can cause data and intellectual property theft. Vehere's AI Network Security looks for behaviour anomalies to detect lateral movements and allows a security administrator to find and stop APTs at the earliest.
Communication on Non-standard Port
Vehere's AI Network Security monitors networks for encrypted communication. For e.g., SSH, SSL/TLS using non-standard ports or set to alert on DPI detection for SSH or SSL/TLS application with ports not equal to standard ports.
Communication on Non-standard Port
Vehere's AI Network Security monitors networks for encrypted communication. For e.g., SSH, SSL/TLS using non-standard ports or set to alert on DPI detection for SSH or SSL/TLS application with ports not equal to standard ports.
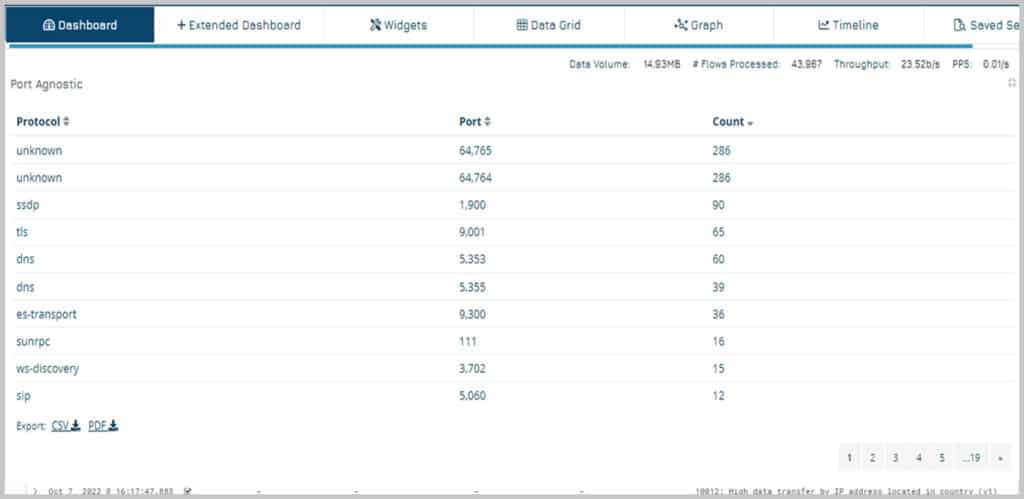
Proactive Threat Hunting
On any network, there will be instances of suspicious activities. They can sometimes indicate advanced threats and targeted activities. Vehere's AI Network Security with Threat Hunting & Alert Forensics enables an extremely fast search engine that helps quickly determine activities of interest based on network metadata and retrieval of interesting artifacts using the same framework without reconstructing every session. It speeds up analysts’ activities by providing them with the required intelligence to identify activities and artifacts of interest.

Proactive Threat Hunting
On any network, there will be instances of suspicious activities. They can sometimes indicate advanced threats and targeted activities. Vehere's AI Network Security with Threat Hunting & Alert Forensics enables an extremely fast search engine that helps quickly determine activities of interest based on network metadata and retrieval of interesting artifacts using the same framework without reconstructing every session. It speeds up analysts’ activities by providing them with the required intelligence to identify activities and artifacts of interest.
