AI Network Security
Vehere Network Security stands at the forefront of cybersecurity solutions, offering a powerful combination of Network Detection & Response (NDR) and Network Forensics (NF) capabilities.
Wirespeed Visibility
Wirespeed Visibility and Analysis from Layer 2 to Layer 7 leveraging advance AI/ML to provide real-time actionable alerts.
Real-Time Anomaly Detection
Location and device agnostic user and application profiling for improved visibility, behavior modelling and eventually resulting in better anomaly detection. Automated port agnostic protocol detection of thousands of protocols leading to accurate application detection and response.
Intelligent Response
Full contextual and one-click investigation workflows for every detection. Leverages artificial intelligence to immediately terminate harmful connections and contain network threats.
Vehere’s cutting-edge AI Network Security is a unified solution of Network Detection and Response (NDR) and Network Forensics (NF). It helps strengthen the security posture of enterprises by using machine learning, rule-based techniques and advanced analytics.
Vehere NDR detects abnormal system behaviours by leveraging behavioral analytics/AI-ML. It detects and contains post-breach activity such as ransomware, APTs, insider threats or lateral movements.
Vehere NF supports security incident response and investigation of source of an incident, analyzes and reconstructs attack timelines, and provides evidence for legal proceedings.
A unified solution that helps enterprises secure their networks through real-time detection, threat hunting and full digital forensics.
Full Visibility with Lossless Packet Capture ensuring zero blind spots
Continuous analysis of both raw network packets and flow traffic in east-west and north-south networks
Port Agnostic protocol detection for over 5000 protocols
Threat Intelligence Integration – Hunting 2 million IOCs at line rate
Zero Day Defender – Next-gen sandboxing to detect Zero-Day malware at Hour Zero
Automated Forensics & security data lake ensuring compliance and actionable insights
Patent-pending Indexed-Raw technique for fast retrieval of packets
Security Initiatives
Network Detection & Response
Network Detection & Response detects abnormal system behaviors by leveraging bahavioral analytics/AI-ML. It detects and contains post-breach activity such as ransomware, APTs, insider threats or lateral movements.
Network Forensics
Network Forensics supports security incident response and investigation of source of an incident, analyzes and reconstructs attack timelines, and provide evidence for legal proceedings.
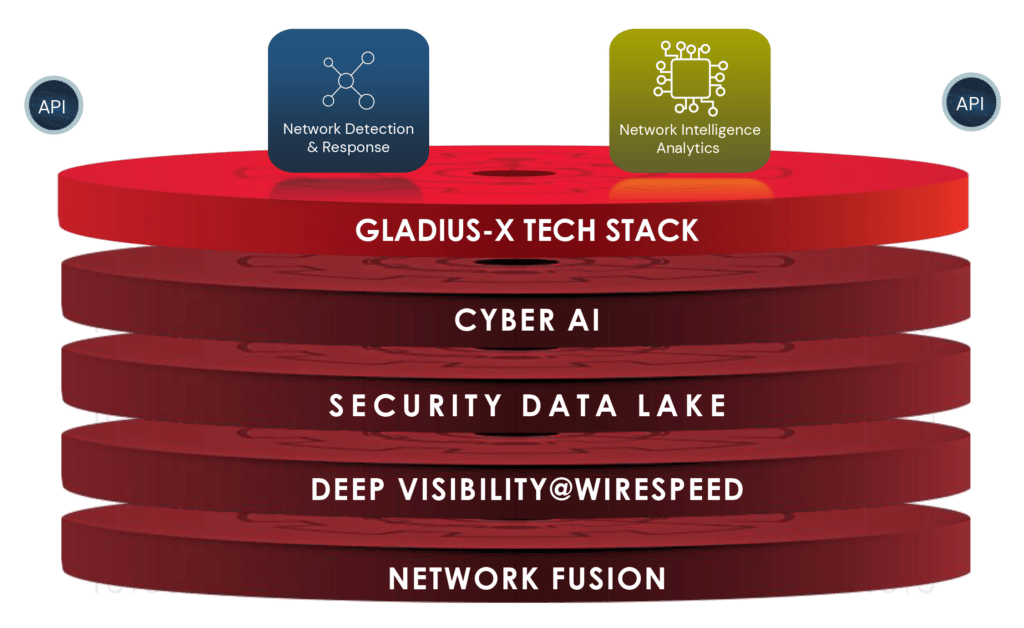
Gladius-X: Vehere's Tech-Stack
'Gladius-X' is Vehere’s exclusive intellectual and proprietary tech-stack for fighting against deadliest threat actors and dreadful anomalies.
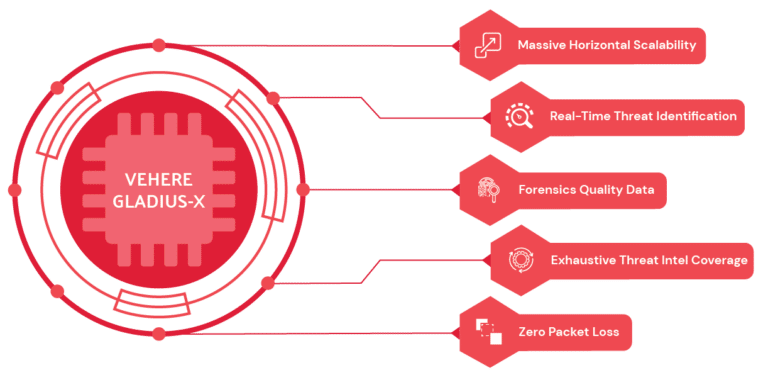
Gladius-X Differentiators
Security Use Cases
Detecting Alarming Activities on Network
Detecting Alarming Activities on Network The longer an attack on a network remains unknown, the more damaging it can be. Vehere AI Network Security is able to quickly show the top alarming activities on a network. This allows for quick investigation and mitigation of potential attacks. The solution prioritizes the threats to decrease Mean Time to Resolution (MTTR).
Investigating Hosts Using the Most Bandwidth
Investigating Hosts Using the Most Bandwidth Organizations need to identify hosts consuming the most bandwidth across the whole network in a business unit or at a specific site. Vehere's AI Network Security Explore module enables users to determine how much bandwidth a host, a host group, or a particular site is consuming. This feature also shows the most used applications or services in a network.
Using Report Module for Performance Analysis
The Report module is essentially used in producing reports comprising the most relevant alarms, events, and activities for a user or team of network operators. This feature allows for report templates to be customized, fitting the requirements of multiple teams, and enabling them to use the detections and insights received more effectively.
Detecting Lateral Movement
Once an attack bypasses the perimeter, it can move through a network laterally, which is a characteristic of an Advanced Persistent Threat (APT). It can cause data and intellectual property theft. Vehere's AI Network Security looks for behaviour anomalies to detect lateral movements and allows a security administrator to find and stop APTs at the earliest.
Communication on Non-standard Port
Vehere's AI Network Security monitors networks for encrypted communication. For e.g., SSH, SSL/TLS using non-standard ports or set to alert on DPI detection for SSH or SSL/TLS application with ports not equal to standard ports.
Proactive Threat Hunting
On any network, there will be instances of suspicious activities. They can sometimes indicate advanced threats and targeted activities. Vehere's AI Network Security with Threat Hunting & Alert Forensics enables an extremely fast search engine that helps quickly determine activities of interest based on network metadata and retrieval of interesting artifacts using the same framework without reconstructing every session. It speeds up analysts’ activities by providing them with the required intelligence to identify activities and artifacts of interest.










