CVE-2022-30525 Zyxel Firmware Remote Command Injection – Executive Summary A command injection vulnerability in the CGI program of some firewall versions could allow an attacker to modify specific files and then execute some OS commands on a vulnerable device. The ...
CVE-2022-30525 Zyxel Firmware Remote Command Injection – Executive Summary
A command injection vulnerability in the CGI program of some firewall versions could allow an attacker to modify specific files and then execute some OS commands on a vulnerable device. The vulnerability, identified as CVE-2022-30525 affects Zyxel firewalls supporting Zero Touch Provisioning (ZTP), which includes the ATP series, VPN series, and the USG FLEX series (including USG20-VPN and USG20W-VPN). This vulnerability allows an unauthenticated and remote attacker to achieve arbitrary code execution as the nobody user on the affected device.
CVE-2022-30525 Zyxel Firmware Remote Command Injection Vulnerability
Zyxel USG FLEX, VPN and ATP device’s firmware is vulnerable to a remote OS command injection vulnerability. Refer to the link below* for information on the exact firmware versions affected by this vulnerability and remedial steps. This vulnerability was actively exploited in 2022. Zyxel devices without the updated firmware will allow an unauthenticated person to remotely execute commands on the device as the user ‘nobody’. The vulnerability is exposed through the /ztp/cgi-bin/handler CGI. An HTTP POST request invoking the command setWanPortSt can have bash commands appended to a parameter value passed to the setWanPortSt command after prepending a semi-colon to the bash command. This is a typical OS command injection technique. The following screenshot demonstrates an example:
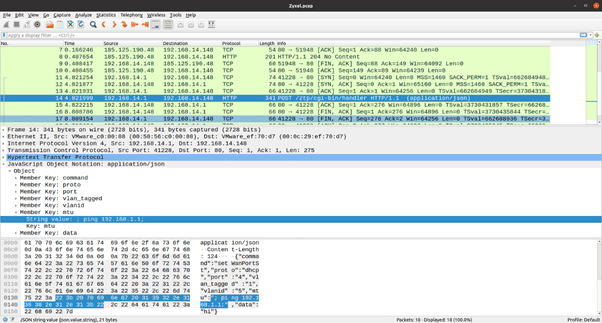
In packet number 14, an HTTP POST request is sent with JSON content to the ztp/cgi-bin/handler CGI. One of the Key passed in is the “mtu” field, which has “; ping 192.168.1.1” as the value. This will invoke the ping command on a vulnerable version of Zyxel devices.
Vehere Network Detection and Response: Protection Against Threat’s Past and Present
Vehere’s research wing, Moon Treader, actively researches new vulnerabilities and malware outbreaks in order to improve the detection efficacy of its NDR solution. Vehere NDR’s Rule Engine is constantly updated to detect threats like the one discussed in this blog.
In addition to a comprehensive Rule Set that guides the Rule Engine in detecting attacks and behavior anomalies, the NDR’s ML engines are trained to detect behavioral anomalies in customer networks. This, combined with a comprehensive set of NDR enhancements to detect lateral movement activity in a network, enables customers to get a holistic view of any violation of their computing assets and deter the progress of the attack.
* https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-30525









