In the first part of our series on lateral movement detection, we took a brief look at the SAMR Service in Windows, and the threat posed to a network if this service is accessible. An attacker with sufficient privileges can ...
In the first part of our series on lateral movement detection, we took a brief look at the SAMR Service in Windows, and the threat posed to a network if this service is accessible. An attacker with sufficient privileges can query this service to gather user-account information. This type of group information is useful for the information-gathering step when staging an attack.
In this part of the series, we will try to understand what the Service Control Manager Remote Protocol, or SCMR, is and how it is used by attackers to start, stop, and launch services remotely.
Windows Service Control Manager Remote Protocol
The Service Control Manager Remote Protocol is a service that enables an administrator to remotely manage services running on the system. The Windows Active Directory service, the Computer Browser service, and the Remote Registry service are a few of the hundreds of services that could be running on a Windows machine.
The SCMR holds the configuration for all services running on the system and is the single point through which an administrator or an administrative tool can be used to remotely manage services on a system. What this also means is that an unauthorized person with sufficient privileges can remotely connect to the SCMR service and control a service of their choice. This is not limited to controlling existing services on the remote system but also setting up and launching unwanted applications.
PsExec is an example of one such application. Though it was developed for administrative purposes, its use is common among threat actors for lateral movement.
In the second part of this series, we’ll look at tools like PsExec and how they work with the Pass-The-Hash technique. In the next section, we will see how the SCMR service can be used to remotely launch the Remote Registry service.
Remotely Controlling a Disabled Service
An attacker can even remotely control a disabled service. The Windows Remote Registry Protocol is a service that enables an administrator to remotely query, modify, or delete the registry of a Windows machine. For an attacker, access like this opens a plethora of attack techniques. The attacker could modify the registry settings to have applications of the attacker’s choosing loaded, stop programs, control how DLLs are loaded, access the SAM database in the registry, etc. This service is by default turned off. However, an attacker with access to the SCMR service can have the Remote Registry service on a remote system enabled and started, thus allowing the attacker complete control over the registry of that system.
The packet capture in the following figures shows the series of packet exchanges that can lead to the Remote Registry service being started.
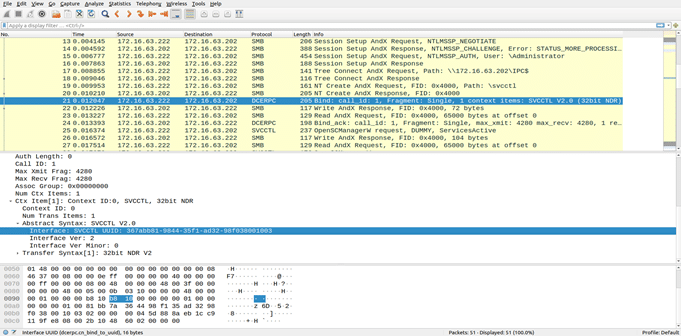
The SCMR service is what’s called a Microsoft Remote Procedure Call, or MSRPC, service. It is accessed through an MSRPC UUID interface operating over an SMB named pipe. A series of handshakes are needed before any MSRPC service can be called upon. In the above screenshot, packet number 19 is where a request is made to access the named pipe SVCCTL, through which access to SCMR MSRPC UUID can be obtained. In packet number 21, a bind operation is requested with the SCMR service. A successful bind provides access to procedure calls exposed by the service. This bind call must go through the SVCCTL named pipe, and so it is handed a handle obtained from packet number 20, which is the response packet to the handshake request in packet number 19.
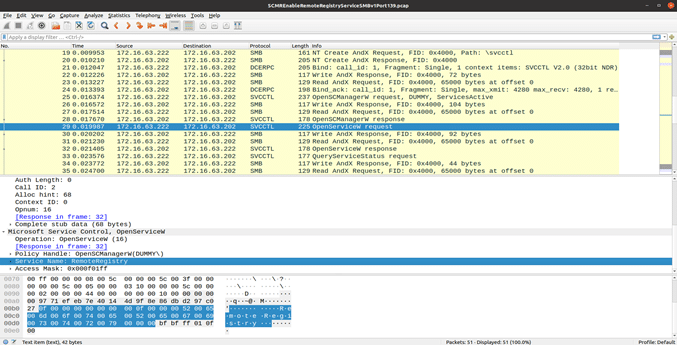
In the above screenshot, one will observe an MSRPC call “OpenServiceW” in packet number 23, and in the bottom panel, one will see the string “RemoteRegistry”. This call obtains a handle for the Remote Registry service, which by default is off in Windows. After obtaining a handle to the shutdown service in packet 39, there is an MSRPC call “StartServiceW”, which issues a command to SCMR to start the RemoteRegistry service. Once the service has started, the attacker has numerous ways to infiltrate the target host and, more specifically, achieve persistence, as we will see in the upcoming part on the Remote Registry Protocol service.
Vehere Network Detection & Response solution detects any attack against the SCMR service through the following rule:
TI10137 SCMR Enable Remote Registry access service SMBv2 Lateral Movement
The following screenshot shows the alert generated by the rule in the face of a malicious SCMR activity in a network.
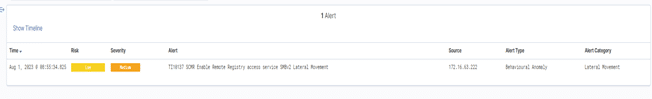
Vehere Network Detection and Response (NDR) Rules for Lateral Movement
In the previous sections, the SCMR service was introduced, and the dangers of it were illustrated by showing how a disabled service like the Remote Registry can be controlled by an attacker. Moon Treader, Vehere’s security research wing, keeps these lateral movement rules updated to have coverage for the latest techniques employed by threat actors and malware. In the next part of this series, we will understand how the Remote Registry service works and how it can be used by attackers to launch code remotely. Until then, be safe and stay tuned!









