In the second installment of our lateral movement detection series, we briefly examined the SCMR Service within the Windows environment, and the threat posed to a network if this service is accessible. An attacker with sufficient privileges can control critical ...
In the second installment of our lateral movement detection series, we briefly examined the SCMR Service within the Windows environment, and the threat posed to a network if this service is accessible. An attacker with sufficient privileges can control critical services on a remote system, launch services on a remote system, and ultimately control critical behavioral aspects of the system.
In this part of the series, we will try to understand what the Windows Remote Registry Protocol is and how it is used by attackers to query system settings, control a system’s behavior, achieve persistence, and steal credentials.
Windows Remote Registry Protocol:
The Windows Registry is a hierarchical database that stores system configuration information and controls a lot of aspects of a Windows system, like booting, installed software configuration, user settings, settings for the currently logged-in user, etc. These configurations are stored across what are called registry hives. The Windows registry has five registry hives, which are as follows:
- HKEY_CLASSES_ROOT: Among other configurations, the most important setting under this hive is the file association configuration, which is used by the operating system to associate software with a file extension. When a user double-clicks on a file, this file association information is used to determine the appropriate software to render the file.
- HKEY_USERS: For each user that is created on the system and logs into it, this hive contains the user profile and the user’s preferences.
- HKEY_CURRENT_USER: This hive contains the user profile and preferences for the currently logged in user. This hive is populated with entries from the HKEY_USERS hive entry for the user logged in.
- HKEY_LOCAL_MACHINE: This hive contains settings for installed software, drivers, and general hardware settings that apply to all users.
- HKEY_CURRENT_CONFIG: The hardware configuration for the system is stored under this hive.
Registry entries are stored as Key-Value pairs. Keys can have subkeys, which in turn can have more subkeys, and information can be stored under these subkeys as Subkey-Value pairs. Each value is stored as a Name-Data pair with the Type information.
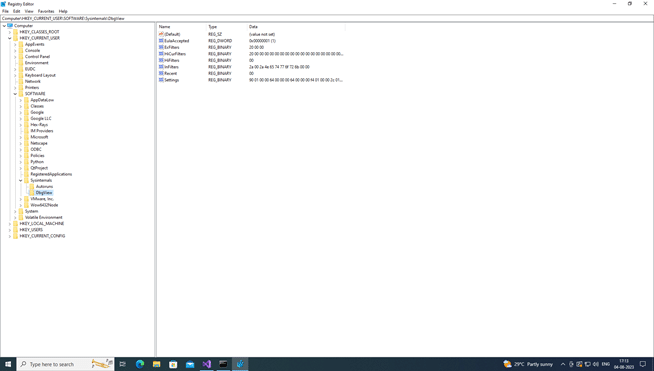
The following screenshot shows the values under the subkey “DbgView”, which comes under the HKEY_CURRENT_USER hive:
Windows Registry and Threat Actors:
Over the years and decades since the introduction of the Windows Registry, it has been the target of malware and threat actors to achieve various goals such as credential harvesting, achieving persistence, disabling security software, deploying fileless malware, etc.
To elaborate on a few of such cases, the SAM subkey under HKEY_LOCAL_MACHINE has the SAM database mapped into it. An attacker with sufficient privileges can have user account information and NTLM hashes dumped from this location. Registry keys like the “Run” key, “RunOnce” key, and “WinLogon” key under HKEY_LOCAL_MACHINE and HKEY_CURRENT_USER are often used by malware to have malicious payloads persist in the system and auto-execute in the event of a reboot or user login. A fileless malware can copy an encoded version of its payload to a registry key instead of dropping it onto the file system, which could trigger an AV scan.
With the Remote Registry Protocol being accessible as an MSRPC service, a remote attacker with sufficient privileges can perform the previously mentioned actions on a remote system. In Part II of this series, we saw how the SCMR service can be used to enable the Remote Registry service, which by default is disabled.
Persistence and Backdooring of Application via AppInit_DLLs Registry Setting:
The AppInit_DLLs value under HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Windows can be used to load a malicious DLL into the address space of a process every time the process is launched. An attacker with sufficient privileges can upload a malicious DLL to a remote system. Next, the attacker can create an AppInit_DLLs entry under HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Windows. This will ensure the malicious code in the DLL persists. In addition, the attacker could use this DLL to hook into Windows API calls.
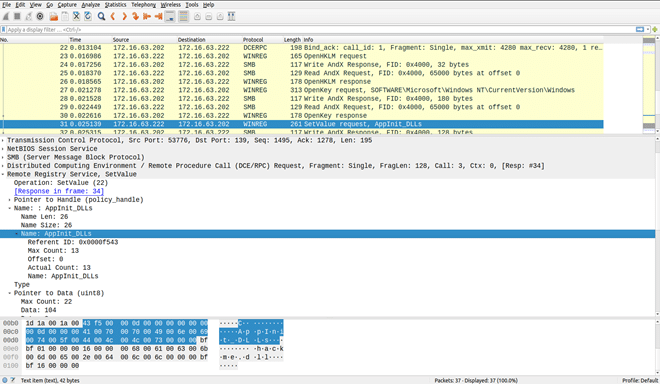
In the screenshot above, we can observe the OpenKey RPC call in packet number 27 that obtains a handle to the key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Windows on a remote system. Next, the attacker calls the MSRPC operation RegSetValue in packet number 31 to create the AppInit_DLLs entry point for a DLL named hackme.dll. With this setting in place, every time a process is started, this DLL gets loaded, and any code in the DLL’s initialization function gets executed.
Persistence via the Run Key Registry Setting:
The Windows Registry has a variety of keys often referred to as the “Run” keys. A registry value setting under this key ensures the executable the “Value” setting points to gets executed and persists on the system.
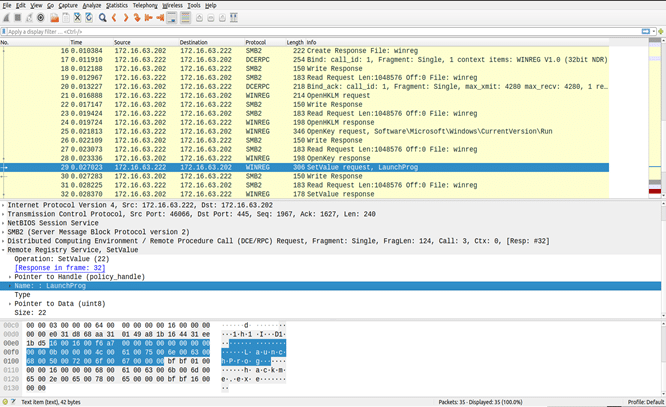
In the screenshot above, we can observe the OpenKey RPC call in packet number 25 that obtains a handle to the key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run. Next, the attacker calls the MSRPC operation RegSetValue in packet number 29 to create the value “LaunchProg” under this key and points this value to “hackme.exe”. With this setting in place, every time a user logon event occurs, the program “hackme.exe” gets executed.
The previous two examples are just a few of the many registry entries that an attacker can remotely access or modify to achieve persistence, steal credentials, or control system behavior. It is important to ensure that services like the Remote Registry Service are not enabled, and traffic to such services on workstations should be treated as suspicious.
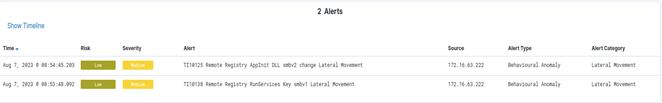
Vehere Network Detection & Response solution detects any lateral movement activity that leverages the Remote Registry Service. The following screenshot shows alerts generated by the Lateral Movement detection rules when a registry editing operation is under way to set the AppInit_DLLs or the RunServices value on a remote system.
Vehere Network Detection and Response (NDR) Rules for Lateral Movement
In the previous sections, the Remote Registry Protocol service was introduced, and the perils of unrestricted access to this service were illustrated by showing how persistence can be achieved by modifying the AppInit_DLLs and Run key entries under the Windows registry. Moon Treader, Vehere’s security research wing, keeps these lateral movement rules updated to have coverage for the latest techniques employed by threat actors and malware.
In the next part of this series, we will understand the role of NTLM in SMB authentication and how attacks like Pass-the-Hash exploits weaknesses in the NTLM protocol to achieve code execution without needing the password to a user account.









