CVE-2020-1472 Zerologon– Executive Summary Microsoft issued a security update, known as CVE-2020-1472 Netlogon Elevation of Privilege Vulnerability, in August 2020 to address a new elevation of privilege (EoP) vulnerability dubbed “Zerologon.” This vulnerability received a perfect score of 10.0 on ...
CVE-2020-1472 Zerologon– Executive Summary
Microsoft issued a security update, known as CVE-2020-1472 Netlogon Elevation of Privilege Vulnerability, in August 2020 to address a new elevation of privilege (EoP) vulnerability dubbed “Zerologon.” This vulnerability received a perfect score of 10.0 on the Common Vulnerability Scoring System (CVSS) and was classified as “critical” by Microsoft for security purposes.
CVE-2020-1472 Windows NetLogon Service Privilege Escalation
Though this vulnerability dates back to August 2020, it is still being actively exploited and used by malware as part of its lateral movement arsenal *. The NetLogon service is used by Active Directory to authenticate domain users and machines, and apply policies associated with the users and machines in the domain.
The NetLogon authentication process has a flaw in its implementation of the AES-CFB8 cryptographic algorithm. By default, the implementation accepts a 16-byte Initialization Vector (IV) which can all be zeros. A machine authenticating itself to the domain controllers uses this zero IV to generate an 8-byte client-challenge of all zeros and, as part of the NetLogon handshake, has this challenge sent to the domain controller in the NetrServerReqChallenge MSRPC request.
The server generates an 8-byte server-challenge and sends it in response to the NetsServerReqChallenge MSRPC request. The authenticating machine next uses the 8-byte client-challenge it generated, which is all zeros in an attack scenario, and its machine login credential as key to generate a “Session Key”.
In an attack scenario, the attacker does not know the machine credentials. With this “Session Key” and the client-challenge, the client generates a NetLogon credential, which is sent in the client credential field of a NetrServerAuthenticate3 MSRPC request. The domain controller uses the client-challenge that it earlier received and the stored credential of the machine to generate a “Session Key” at its end.
With this “Session Key” and the client-challenge the domain controller earlier received, the domain controller computes a value. If this value matches the value in the client credential field of the NetrServerAuthenticate3 request, then the machine get authenticated. The core flaw in this handshake is that the IV is not random, and an all zero IV could, with a probability of 1 out of 256 attempts, lead to the server accepting an 8-byte 0 value for Client Credentials in the NetrServerAuthenticate3 request. An attacker at most needs to send 256 brute force attempts to logon to a domain controller with a NULL credential.
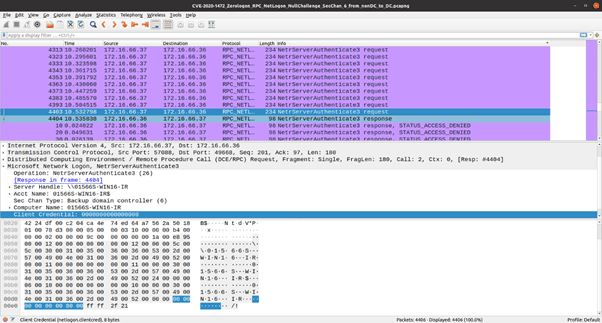
In the screenshot above **, several NetrServerAuthenticate3 requests can be seen with the Client Credential field set to zero. These requests are denied by the server until the point where the server itself ends up computing an all zero NetLogon credential. As seen in the following screenshot, the domain controller eventually responds with a STATUS_SUCCESS code to the logon request.
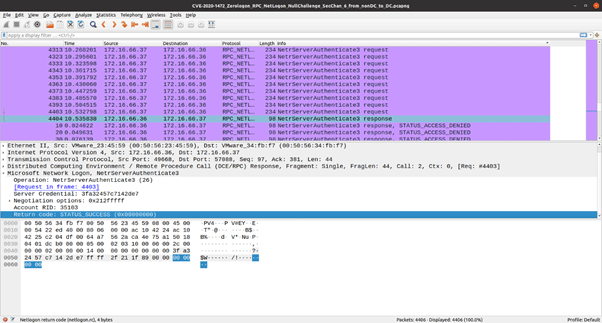
This vulnerability has been assigned a CVSS score of 10. It is trivial to trigger this vulnerability and take complete control over a domain controller. Customers are advised to follow the Microsoft advisory for this CVE and have the patch for this vulnerability applied.
Vehere Network Detection and Response: Protection Against Threat’s Past and Present
Vehere’s research wing, Moon Treader, actively researches new vulnerabilities and malware outbreaks in order to improve the detection efficacy of its NDR solution. Vehere NDR’s Rule Engine is constantly updated to detect threats like the one discussed in this blog.
In addition to a comprehensive Rule Set that guides the Rule Engine in detecting attacks and behavior anomalies, the NDR’s ML engines are trained to detect behavioral anomalies in customer networks. This, combined with a comprehensive set of NDR enhancements to detect lateral movement activity in a network, enables customers to get a holistic view of any violation of their computing assets and deter the progress of the attack.
* https://thedfirreport.com/2022/02/21/qbot-and-zerologon-lead-to-full-domain-compromise/









