CVE-2022-26134 Atlassian Confluence – Executive Summary Volexity discovered suspicious activity on two internet-facing servers using Atlassian’s Confluence Server application on June 2, 2022. Volexity examined the breach and concluded that a remote code execution vulnerability in Confluence Server and Data ...
CVE-2022-26134 Atlassian Confluence – Executive Summary
Volexity discovered suspicious activity on two internet-facing servers using Atlassian’s Confluence Server application on June 2, 2022. Volexity examined the breach and concluded that a remote code execution vulnerability in Confluence Server and Data Center was the cause of the initial breach. The incident details were then reported to Atlassian on May 31, and Atlassian has designated the problem as CVE-2022-26134.
CVE-2022-26134 Atlassian Confluence OGNL Injection Vulnerability
Atlassian Confluence is a content collaboration and management software. In June 2022, it was reported that the software is vulnerable to an OGNL injection attack. Attackers can leverage this vulnerability to have the code executed on the server side. The following types of software are affected:
· Confluence Server
· Confluence Data Center
OGNL is an expression language that can get and set properties of Java Objects. Jakarata EE, formerly Java Platform Enterprise Edition, uses Expression Language for embedding and evaluating expressions in web pages developed using Jakarta EE. If the web server does not perform sanity checks on an input provided by a user, which in turn is sent to the OGNL library for expression evaluation, the server will be vulnerable to OGNL injection.
A server running a vulnerable version of Confluence will have an attacker-provided expression evaluated. All an attacker has to do is submit a GET request to the server’s IP address with the following content as part of the GET parameter.
The exec portion of the above parameter can contain any command that can be executed by the end server under the privilege of the hosting server process. A typical example seen in the wild is using PowerShell on a Windows server running Confluence to download malware and have it executed. There have been reports of Webshells being uploaded onto vulnerable servers.
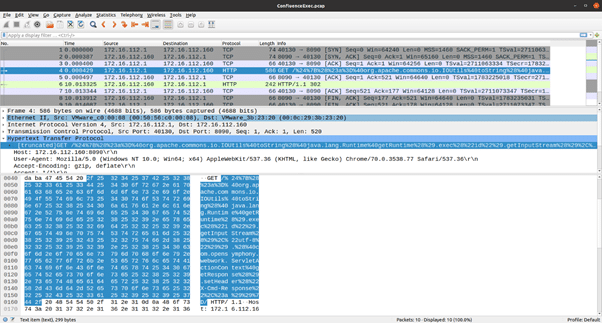
In the above screenshot, the highlighted packet shows an HTTP GET request being forwarded to a vulnerable server and an “exec” request that will be evaluated by the OGNL parser, leading to code execution. At the time of the disclosure of the vulnerability, thousands of exploit attempts per day were being tracked. *
Vehere Network Detection and Response: Protection Against Threat’s Past and Present
Vehere’s research wing, Moon Treader, actively researches new vulnerabilities and malware outbreaks in order to improve the detection efficacy of its NDR solution. Vehere NDR’s Rule Engine is constantly updated to detect threats like the one discussed in this blog.
In addition to a comprehensive Rule Set that guides the Rule Engine in detecting attacks and behavior anomalies, the NDR’s ML engines are trained to detect behavioral anomalies in customer networks. This, combined with a comprehensive set of NDR enhancements to detect lateral movement activity in a network, enables customers to get a holistic view of any violation of their computing assets and deter the progress of the attack.
https://www.akamai.com/blog/security-research/atlassian-confluence-vulnerability-observations









