See you at Milipol Paris 2023!
Leading Event for Homeland Security and Safety
14–17 November 2023,
Paris Nord Villepinte, France
We will be at Milipol India 2023
The Leading International Event for Internal Security in India
Visit us at Stall No. 11342
26-28 October 2023, Pragati Maidan Exhibition Centre, New Delhi
Protecting your Nation: Defending your Cyberspace, Respecting your Privacy
Acknowledged by Gartner®
Vehere included under example of NDR Vendors in two Gartner® reports
Emerging Tech: Top Use Cases for Network Detection and Response
Emerging Tech: Security — Adoption Growth Insights for Network Detection and Response
Comprehensive visibility and protection across your critical areas of risk: Networks, Cloud, Workloads and Data.
Visibility: Zero blind spot: Monitor Full Packet Capture at datacentre and Flow at branch level. Real-time threat detection at NIC
Cyber Threat Intelligence: Make Cyber Threat Intelligence Feed Actionable. Consume Millions of IOC’s – IOA’s
Forensics & Response: Unscripted Threat Hunting for Emerging Threats. 1-Click Evidence for Incident Response

Manage cyber risks while reducing incident response costs by over 60%.
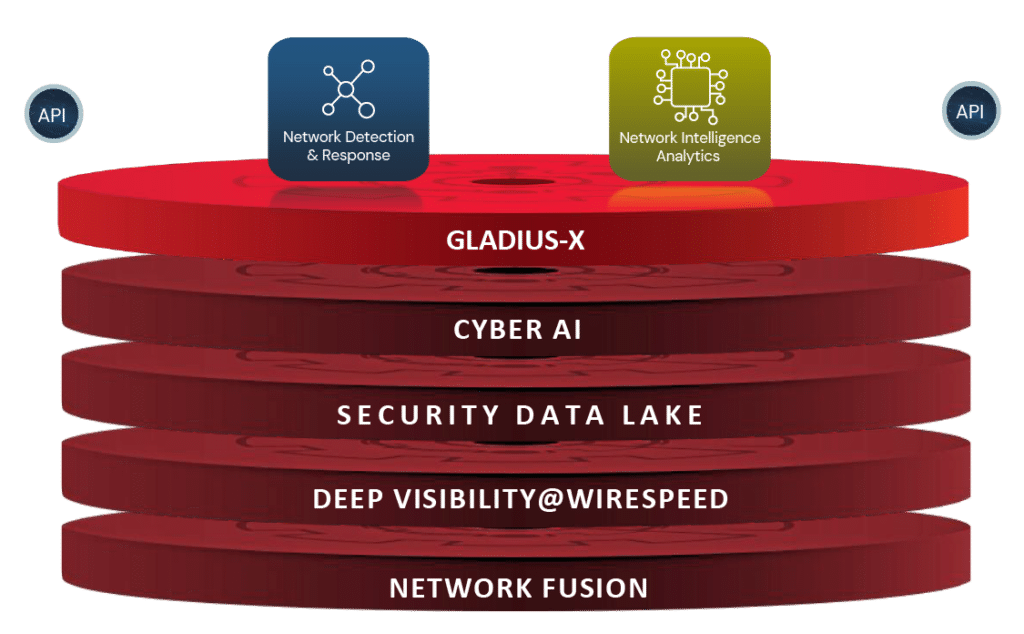
Vehere's Gladius-X
The "Gladius-X", a Vehere’s exclusive intellectual and proprietary technological stack for fighting against deadliest threat actors and dreadful anomalies.
Visibility
5000+
Protocols Supported for the widest coverage
Response Time
0.5s
From Detection to Forensics
CTI Consumption
1 Mn+
Makes the CTI Feeds from Paid Sources, Open Sources, or both actionable
One platform
2
Detection, CTI Integration and Forensics & Response merged in one entity
Why Vehere?
Vehere is boldly merging the realms of national security and enterprise security through a single, powerful platform
Gain 360-degree visibility to see cyber threats before they escalate into breaches.
Get real-time insights into past, present, and future threat activity with probabilistic generative AI, ML, and full forensics.
Detect, prioritize, and stop threats with technology that simplifies network security and saves both time and money.
Stay ahead of modern cyberattacks with Vehere's products

Vehere Network Detection & Response
Full contextual information with ML threat intelligence
Probabilistic generative AI to gain actionable intelligence

Vehere Network Intelligence
Analytics
Analyze using metadata, both real-time and historical

Vehere Network Detection & Response
PACKETWORKER
• Full contextual information with ML threat intelligence
• Increased efficiency of SecOps
• Cost savings because of Network agnostic, flexible deployments

Vehere Network Intelligence
Analytics
IntelliWorker
• Lossless capture with 2X more visibility than others
• Analyze using metadata, both real-time and historical
• Probabilistic generative AI to gain actionable intelligence
Vehere’s best-in-breed technology for network security
Fortifying the world’s most daunting networks
Detect Suspicious Traffic
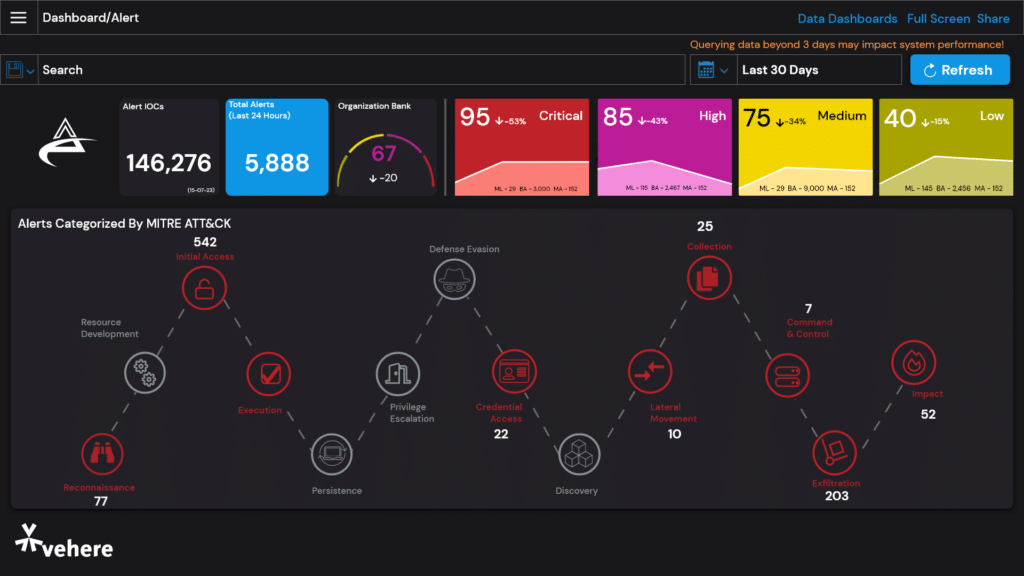
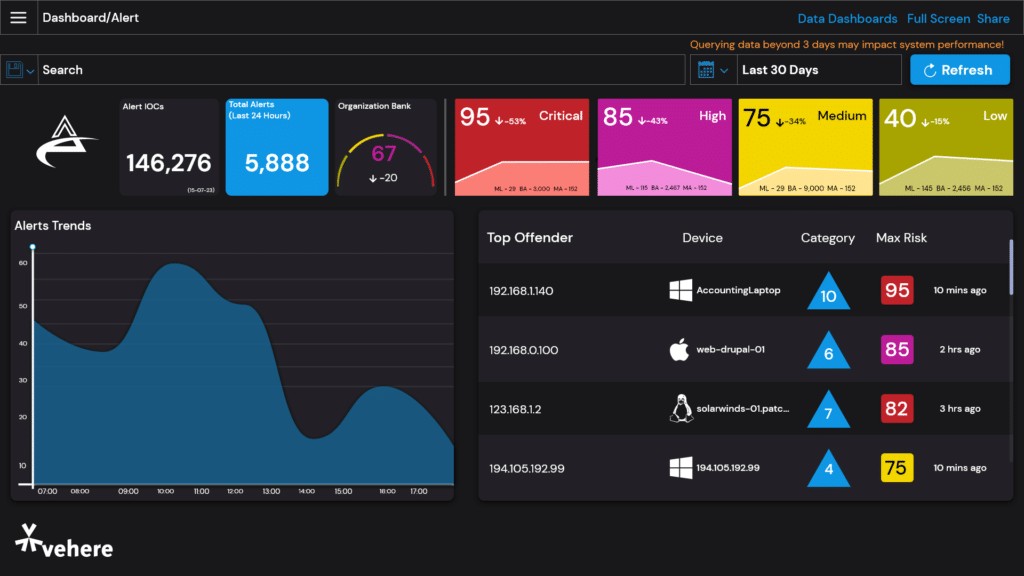
Our cutting-edge Network Detection and Response (NDR) solution implements machine learning and behaviour-based techniques to help enterprises detect suspicious traffic that other security tools are missing.
Proactive Threat Hunting
Proactively search for cyber threats that are lurking undetected in the network. With the help of our Network Detection and Response (NDR) solution, dig deep to find malicious actors in your environment that have slipped past your initial network security defenses.
Forensics
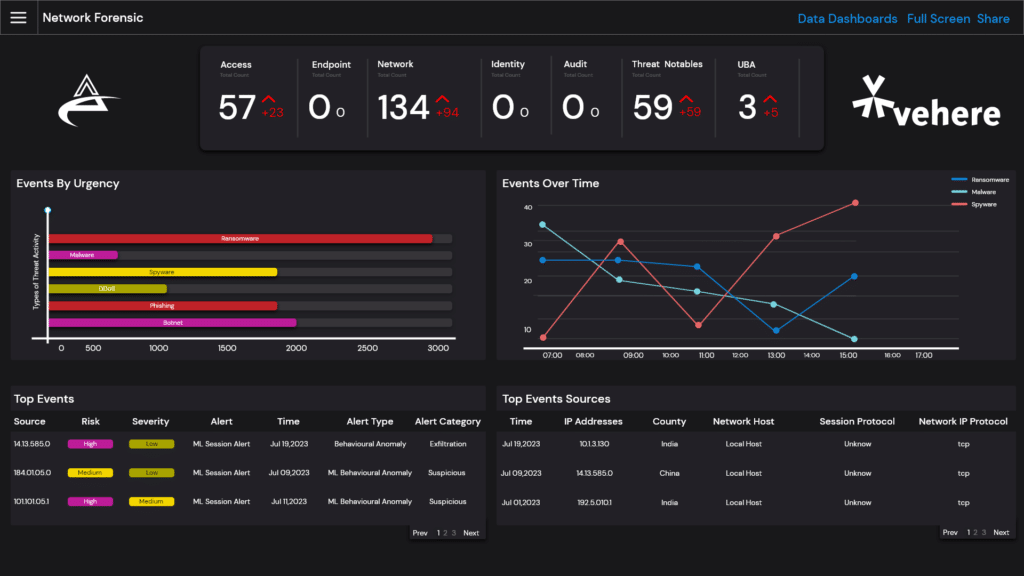
Vehere's powerful Network Forensic indulges in retrospective analysis through stored real-time packet data for unearthing the tracks of a threat actor. Ensure an insightful investigation using a combination of raw captures and metadata.
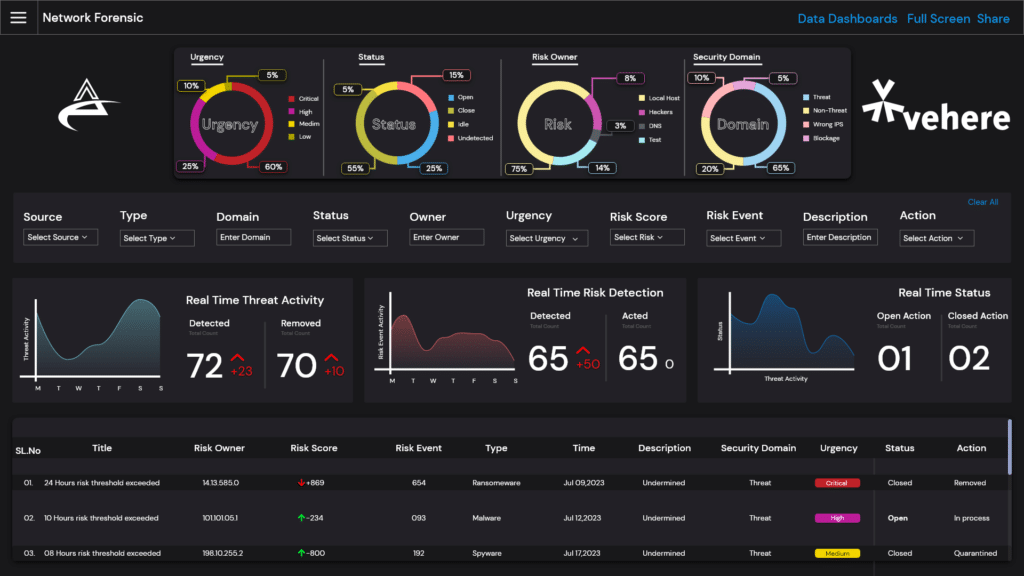
Advanced Network Forensics
Delve into the world of insights and retrospective analysis leveraging real-time analysis of telemetry & packet data, and North-South and East-West traffic. Get a real-time view of the relevant details and insights into user activity for better triage.
Gaining Rapid Traction
100%
Regions Defense & Intelligence Communities rely on our technology to Improve Security Posture.
TOP 10
Global Telecommunication companies use Vehere’s technology
TOP 8
Financial Institutions rely on our technology
TOP 3
Smart City Projects use Vehere's technology
Market Leader with a Marquee Cross-Sector Client Base
What's Dawn Treader up to?
Check out Vehere’s security research wing, Dawn Treader’s latest findings!
Welcome to the future of cybersecurity with Vehere!
Vehere is a revolutionary cybersecurity company, boldly merging the realms of national security and enterprise security through a single, powerful platform. Established in 2006, Vehere is a global corporation securing clients at global scale.
Trusted by world's topmost organizations
Vehere is a cyber network intelligence company, a frontrunner in enabling Cyber Situation Awareness. CSA helps in achieving complete, real-time visibility and comprehensive insights into network activities, thereby assisting in better decision-making.
Dawn Treader Backed by Actionable Intelligence
The go-to Research Wing by leveraging advanced threat intelligence, quick incident response, cyber-security expertise and backed by Vehere Interactive technology.


